Understanding the role of miners in maintaining the security of blockchain networks. – Understanding the role of miners in maintaining the security of blockchain networks is crucial to grasping how these decentralized systems function. Miners aren’t just verifying transactions; they’re the backbone of a system designed to resist manipulation and attacks. This exploration delves into the intricate mechanisms they employ, the challenges they face, and their vital contribution to the overall trustworthiness of blockchain technology.
We’ll examine how miners use proof-of-work to secure the network, earning rewards for their computational efforts. We’ll also discuss the potential threats, like 51% attacks, and how the decentralized nature of mining helps prevent them. Finally, we’ll look at the future of mining and how technological advancements and evolving regulations might shape its role in blockchain security.
Miners’ Role in Transaction Verification and Block Creation
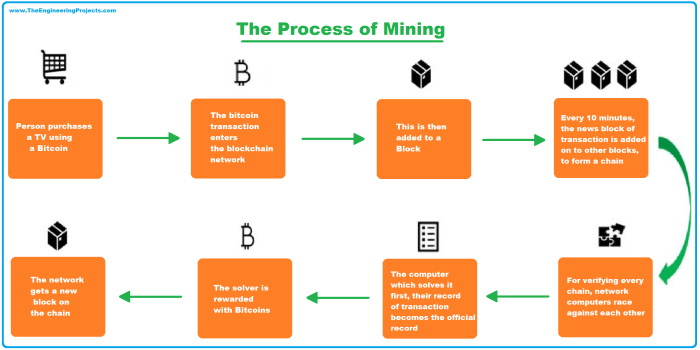
Miners are the backbone of many blockchain networks, responsible for verifying transactions and adding them to the permanent, tamper-proof record. Their actions directly impact the security, speed, and overall functionality of the system. Understanding their role is key to grasping how blockchains operate.
Miners perform two crucial functions: verifying transactions and creating new blocks. This involves a complex process of cryptographic hashing, consensus mechanisms, and competition among miners to add the next block to the chain. The incentives for miners, typically cryptocurrency rewards, drive this continuous process, ensuring the blockchain’s ongoing security and growth.
Transaction Verification
Miners don’t simply accept transactions at face value. Before a transaction can be included in a block, it undergoes rigorous verification. This involves checking several key aspects, including the digital signatures to confirm the sender’s authorization, ensuring the sender possesses sufficient funds, and verifying that the transaction hasn’t already been processed or is not attempting a double-spend. This verification process is crucial for maintaining the integrity of the blockchain and preventing fraudulent activities.
If a miner detects an invalid transaction, it’s rejected and not included in the block.
Block Creation
Once a miner has collected a sufficient number of verified transactions, they begin the process of creating a new block. This involves grouping the verified transactions together and applying a cryptographic hash function to the entire set. This hash function produces a unique fingerprint for the block, linking it to the previous block in the chain. The miner then attempts to solve a complex computational puzzle, typically involving finding a number that, when hashed with the block’s data, meets specific criteria (e.g., starts with a certain number of zeros).
This process is known as “mining,” and the first miner to solve the puzzle gets to add the new block to the blockchain and receives a reward.
Impact of Miner Participation on Transaction Speed and Confirmation Times
The number of active miners significantly impacts transaction processing speed and confirmation times. A higher number of miners generally leads to faster block creation and transaction confirmation because more computational power is dedicated to solving the cryptographic puzzle. Conversely, fewer miners can result in slower processing times and longer confirmation times, potentially impacting the user experience and network efficiency. For example, during periods of low miner participation on a network, users might experience delays in transaction confirmations, whereas periods of high miner participation will lead to faster processing and confirmation.
The level of network congestion also plays a role, as a high volume of transactions can increase processing times even with a large number of miners.
Block Creation and Verification Flowchart
The following describes a simplified flowchart illustrating the steps involved:
Step 1: Transaction Broadcasting: Users broadcast their transactions to the network.
Step 2: Transaction Verification by Miners: Miners verify the validity of each transaction.
Step 3: Transaction Pooling: Verified transactions are added to a pool of pending transactions.
Step 4: Block Creation: A miner collects transactions from the pool and creates a new block.
Step 5: Proof-of-Work (or other consensus mechanism): The miner solves a cryptographic puzzle to add the block.
Step 6: Block Broadcasting: The miner broadcasts the new block to the network.
Step 7: Block Verification by Other Miners: Other miners verify the new block’s validity.
Step 8: Block Addition to Blockchain: If valid, the block is added to the blockchain.
Step 9: Reward Distribution: The miner who successfully added the block receives a reward.
The 51% Attack and its Prevention by Miners
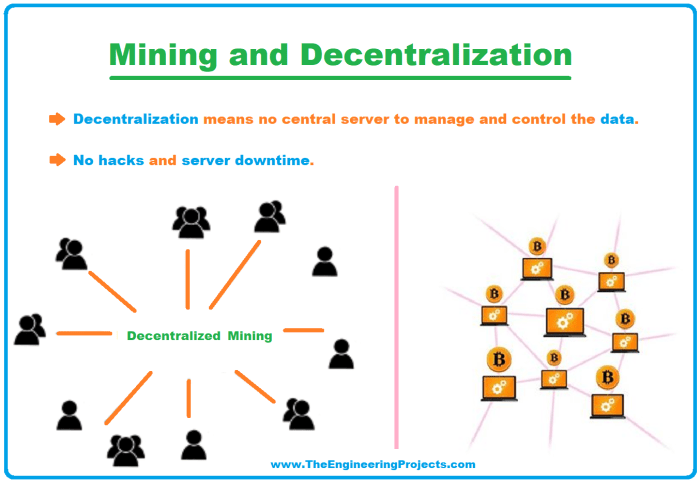
A 51% attack, also known as a majority attack, is a serious threat to the security and integrity of a blockchain network. It occurs when a single entity or group gains control of more than 50% of the network’s computing power (hash rate). This allows them to manipulate the blockchain by, for example, reversing transactions, preventing legitimate transactions from being confirmed, or creating competing chains to double-spend cryptocurrency.
This undermines the very principles of decentralization and trust that blockchain technology is built upon.The decentralized nature of mining is crucial in mitigating the risk of a 51% attack. Because mining is distributed across many independent miners worldwide, it’s incredibly difficult for any single entity to accumulate the necessary computing power to control a majority of the network.
This makes it computationally and economically infeasible for most attackers to attempt such a large-scale takeover. The more geographically dispersed and independent the miners, the harder it becomes to orchestrate a successful 51% attack.
Decentralization’s Role in 51% Attack Mitigation
The distributed nature of mining across numerous independent miners globally makes it extremely difficult for any single entity or group to amass over 50% of the network’s hashing power. This inherent decentralization acts as a significant barrier against successful 51% attacks. Even if a powerful entity tries to centralize mining operations, the vast geographic spread of miners and the independent nature of their participation make it a costly and complex endeavor.
When investigating detailed guidance, check out Understanding the technical specifications of the Solana blockchain. now.
The cost of acquiring sufficient hardware and maintaining the energy consumption required for such an attack is prohibitive for most. The sheer logistical challenge of coordinating a global network of miners also presents a formidable obstacle.
Difficulty Adjustment Mechanism and 51% Attack Prevention
Blockchain networks employ a difficulty adjustment mechanism to maintain a consistent block creation rate. This mechanism automatically adjusts the difficulty of mining new blocks based on the network’s current hash rate. If the hash rate increases (e.g., more miners join the network), the difficulty increases, making it harder to find a solution and mine a block. Conversely, if the hash rate decreases, the difficulty decreases.
This dynamic adjustment prevents a single entity from gaining an unfair advantage by simply increasing their hashing power. A sudden surge in hashing power by an attacker attempting a 51% attack would immediately trigger a difficulty increase, making the attack considerably more challenging and resource-intensive.
You also can investigate more thoroughly about The future of decentralized finance (DeFi) built on blockchain technology. to enhance your awareness in the field of The future of decentralized finance (DeFi) built on blockchain technology..
Real-world Examples of Miner Participation Preventing Attacks
While documented instances of successful large-scale 51% attacks on major cryptocurrencies are rare, several situations demonstrate how miner participation has thwarted or mitigated potential attacks. For example, during periods of increased network activity or attempted attacks on smaller, less established cryptocurrencies, the collective response of miners to maintain the integrity of the blockchain has been observed. In these cases, the decentralized nature of mining, combined with the difficulty adjustment mechanism, effectively prevented successful manipulation of the blockchain.
While specific details of these events are often kept private for security reasons, the general principle of a large, distributed mining community resisting malicious actors is well established within the cryptocurrency space. The collective actions of miners, even without coordinated efforts, have often proved sufficient to maintain network security and thwart potential attacks.
Mining Hardware and its Influence on Network Security: Understanding The Role Of Miners In Maintaining The Security Of Blockchain Networks.
The hardware used for mining significantly impacts a blockchain network’s security and decentralization. Different types of hardware offer varying levels of computational power, energy efficiency, and accessibility, all of which influence the overall health and resilience of the network. Understanding these factors is crucial to assessing a blockchain’s robustness against attacks and its long-term sustainability.The efficiency and cost of mining hardware directly affect the distribution of mining power.
This distribution is a key factor in determining the level of decentralization within a blockchain network. Highly specialized and expensive hardware can create barriers to entry, leading to centralization, while more accessible hardware can promote a more distributed network. The environmental impact of energy consumption is also a significant consideration.
Types of Mining Hardware and Their Impact on Network Security
Mining hardware has evolved significantly, from CPUs to specialized ASICs. Early Bitcoin mining utilized CPUs and GPUs, offering relatively low hash rates and high energy consumption per unit of computational power. The introduction of ASICs (Application-Specific Integrated Circuits) revolutionized mining, providing significantly higher hash rates and greater energy efficiency for a given level of computational power. However, this specialization also increased the barrier to entry, contributing to the centralization of mining power in the hands of large mining farms.
Field-Programmable Gate Arrays (FPGAs) represent a middle ground, offering some programmability but generally lower hash rates than ASICs.
Energy Consumption and Environmental Implications of Mining Hardware
The energy consumption of mining hardware is a major concern. ASICs, while highly efficient compared to CPUs and GPUs in terms of hash rate per watt, still consume substantial amounts of energy, particularly when deployed at scale in large mining farms. This energy consumption has environmental implications, contributing to carbon emissions and increasing the overall environmental footprint of the blockchain network.
The choice of energy source (e.g., renewable vs. fossil fuels) further impacts the environmental cost. For example, a Bitcoin mining operation powered by hydroelectric energy has a smaller carbon footprint than one reliant on coal-fired power plants. Estimates vary widely depending on the specific hardware, location, and energy source, but the overall energy consumption of Bitcoin mining is a significant and ongoing topic of debate and research.
Centralization Potential Due to High Hardware Costs
The high cost of specialized ASICs creates a significant barrier to entry for new miners. Only large organizations or well-funded individuals can afford the upfront investment in the hardware and the ongoing operational costs, including electricity and maintenance. This leads to a concentration of mining power in the hands of a few large players, potentially compromising the decentralization and security of the network.
A scenario where a small number of entities control a significant portion of the network’s hash rate increases the risk of a 51% attack, even if such an attack remains unlikely given the current distribution.
Pros and Cons of Different Mining Hardware Types
Let’s compare the advantages and disadvantages of different hardware types used for mining:
- CPUs:
- Pros: Relatively low initial cost, readily available.
- Cons: Extremely low hash rate, high energy consumption per unit of computational power, impractical for profitable mining of most cryptocurrencies.
- GPUs:
- Pros: Higher hash rate than CPUs, relatively accessible.
- Cons: Lower hash rate than ASICs, higher energy consumption per unit of computational power than ASICs, becoming less competitive with ASICs.
- FPGAs:
- Pros: Programmable, potentially adaptable to different algorithms.
- Cons: Generally lower hash rate than ASICs, higher cost than GPUs.
- ASICs:
- Pros: Highest hash rate, most energy-efficient per unit of computational power.
- Cons: High initial cost, specialized hardware, not adaptable to different algorithms, contributes to centralization.
The Impact of Mining Pools on Network Security
Mining pools fundamentally alter the landscape of blockchain security by aggregating the hashing power of numerous individual miners. While they offer advantages like increased profitability and more consistent block rewards for participants, their impact on the decentralization and security of the network is a complex and crucial aspect to understand. This section will explore how mining pools operate, their potential risks, and their influence on the overall health of blockchain networks.Mining pools function by combining the computational power of many miners.
Instead of each miner competing individually to solve cryptographic puzzles and earn block rewards, they contribute their hashing power to a shared pool. The rewards are then distributed among the pool members proportionally to their contribution. This system significantly increases the chances of finding a block and earning rewards, especially for miners with limited resources. However, this centralization of mining power raises significant concerns about network security.
Mining Pool Operation and Decentralization
The operation of mining pools directly impacts the decentralization of a blockchain network. Decentralization, a core principle of many blockchains, aims to distribute power and prevent control from being concentrated in the hands of a few entities. Mining pools, by their nature, consolidate hashing power, potentially undermining this principle. A smaller number of large pools effectively control a larger percentage of the network’s mining power, making the network more vulnerable to various attacks and potentially shifting the balance of power away from a truly distributed system.
The more concentrated the mining power becomes within a few pools, the less decentralized the network becomes. This shift can lead to several security and governance concerns.
Risks Associated with Mining Pool Centralization
The concentration of mining power in the hands of a few large mining pools poses several significant risks to network security. One major concern is the increased potential for a 51% attack, even if no single entity controls that much power. A coordinated attack by a few large pools could theoretically allow them to control the network, potentially reversing transactions, censoring information, or even launching double-spending attacks.
Furthermore, the potential for collusion between pool operators presents a serious threat. This could lead to manipulation of the network, prioritization of certain transactions, or the exploitation of vulnerabilities for personal gain. The trust placed in pool operators becomes paramount, and a lack of transparency or malicious actors could severely damage the network’s integrity.
Examples of Large Mining Pools and Market Share
Several prominent mining pools currently hold substantial market share across various cryptocurrencies. For example, (Note: Market share data fluctuates frequently. Specific percentages should be verified from up-to-date resources such as blockchain explorers or reputable cryptocurrency news sites.) These pools, while offering services to many miners, illustrate the level of concentration of mining power. The dominance of a few large pools means that a relatively small number of entities hold significant influence over the network’s security and operation.
Concentration of Mining Power and its Impact on Network Security
The concentration of mining power in a few large pools significantly impacts network security. A higher concentration reduces the network’s resilience to attacks. A smaller number of pools controlling a large percentage of the hash rate means a smaller number of entities need to collude to launch a successful attack. This reduces the overall cost and complexity of potentially malicious activities.
Furthermore, the potential for censorship and manipulation of transactions increases. A powerful pool operator could, in theory, choose to prioritize transactions that benefit them or their clients, potentially neglecting or delaying others. This could lead to unfair advantages and damage the fairness and trust within the blockchain ecosystem.
Future of Mining and Blockchain Security

The future of blockchain security is intrinsically linked to the evolution of mining and the broader technological landscape. Several factors, including technological advancements, alternative consensus mechanisms, and regulatory pressures, will significantly shape how blockchain networks are secured in the years to come. Understanding these forces is crucial for predicting and adapting to the changing dynamics of the blockchain ecosystem.
Technological Advancements Impacting Mining
Several technological advancements hold the potential to reshape the role of miners. Improvements in hardware, such as the development of more energy-efficient ASICs (Application-Specific Integrated Circuits) or the utilization of quantum computing (though still theoretical in its application to mining at scale), could drastically alter the mining landscape. For example, a significant increase in hashing power from more efficient ASICs could lead to a centralization of mining power, potentially impacting network security unless countermeasures are implemented.
Conversely, quantum computing, if successfully applied, could break current cryptographic algorithms, requiring a complete overhaul of blockchain security protocols. This could necessitate a transition to post-quantum cryptography and fundamentally alter the mining process.
Implications of Alternative Consensus Mechanisms
Proof-of-Stake (PoS) and other alternative consensus mechanisms are emerging as potential replacements for the energy-intensive Proof-of-Work (PoW) consensus used by Bitcoin and other cryptocurrencies. PoS systems significantly reduce energy consumption by selecting validators based on their stake in the network rather than computational power. This shift diminishes the role of miners, replacing them with validators who secure the network through their holdings.
The security implications are complex: PoS might be more vulnerable to attacks from large stakeholders, while PoW faces the challenge of energy consumption and its environmental impact. The transition to PoS could lead to a different kind of centralization risk, requiring novel approaches to maintaining decentralization and security. For example, the Ethereum network’s successful transition to PoS demonstrates the viability of this approach, but also highlights the complexities involved in such a large-scale migration.
Regulatory Impacts on Mining and Network Security
Government regulations are increasingly influencing the mining industry. Regulations focused on energy consumption, environmental impact, and tax implications can significantly impact the profitability and geographic distribution of mining operations. For instance, China’s ban on cryptocurrency mining led to a significant shift in mining activity to other countries, impacting the network’s geographic distribution and potentially affecting its resilience. Stringent regulations could stifle innovation and limit the decentralization of mining, while poorly designed regulations could inadvertently create vulnerabilities or favor certain actors.
Future regulations will likely focus on balancing environmental concerns with the economic benefits and technological advancements of blockchain technology.
Timeline of Potential Future Developments, Understanding the role of miners in maintaining the security of blockchain networks.
| Year | Development | Impact on Mining and Security |
|---|---|---|
| 2024-2026 | Increased adoption of PoS and other consensus mechanisms | Reduced reliance on traditional mining; potential shift in security vulnerabilities. |
| 2027-2029 | Development of more energy-efficient mining hardware | Potential increase in hashing power, centralization concerns, and increased competition. |
| 2030-2035 | Increased regulatory scrutiny and standardization of blockchain technology | Potential impact on mining profitability and geographic distribution, increased security standards. |
| Beyond 2035 | Emergence of post-quantum cryptography and new consensus mechanisms | Fundamental shift in mining processes and security protocols; potential for new security challenges and solutions. |
In conclusion, miners are indispensable to the security and integrity of blockchain networks. Their participation, though facing challenges like centralization and energy consumption, forms a critical defense against malicious actors. Understanding their complex role—from transaction verification to mitigating attacks—is key to appreciating the resilience and potential of blockchain technology. As the technology evolves, so too will the role of miners, necessitating continued analysis and adaptation.