Analyzing the security features of different cryptocurrency wallets. – Analyzing the security features of different cryptocurrency wallets is crucial for anyone holding cryptocurrency. This exploration delves into the diverse security mechanisms employed by various wallet types – from hot and cold wallets to hardware solutions like Ledger and Trezor. We’ll compare their strengths and weaknesses, examine the effectiveness of two-factor authentication (2FA), and discuss how to protect yourself from phishing and social engineering attacks.
Understanding these nuances is paramount to safeguarding your digital assets.
We’ll cover everything from choosing the right wallet type based on your risk tolerance and security needs to implementing best practices for password management, software updates, and backup strategies. The goal is to empower you with the knowledge to make informed decisions and keep your cryptocurrency secure.
Types of Cryptocurrency Wallets: Analyzing The Security Features Of Different Cryptocurrency Wallets.
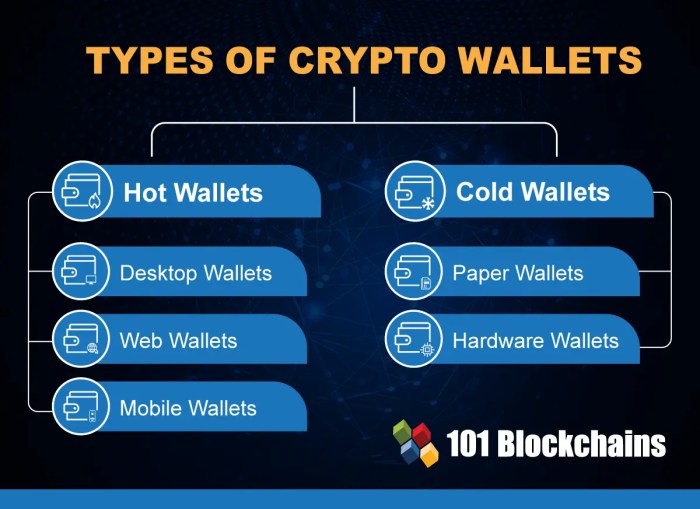
Choosing the right cryptocurrency wallet is crucial for securing your digital assets. Different wallet types offer varying levels of security and convenience, each with its own strengths and weaknesses. Understanding these differences is essential for protecting your investments. This section will delve into the security features of hot, cold, and hardware wallets.
Notice What are the environmental concerns surrounding blockchain technology and cryptocurrency mining? for recommendations and other broad suggestions.
Hot, Cold, and Hardware Wallet Comparison
The primary distinction between cryptocurrency wallets lies in how they connect to the internet. This connection significantly impacts their security. The following table summarizes the key features of hot, cold, and hardware wallets.
| Wallet Type | Security Features | Advantages | Disadvantages |
|---|---|---|---|
| Hot Wallet (e.g., software wallets on smartphones or computers) | Encryption (often AES-256), two-factor authentication (2FA), potentially multi-signature support. Security relies heavily on software and operating system security. | Convenience, easy access to funds, readily available for transactions. | Higher risk of hacking and theft due to constant internet connection. Vulnerable to malware, phishing attacks, and keyloggers. |
| Cold Wallet (e.g., paper wallets, offline software wallets) | Security relies on physical isolation from the internet. Private keys are never exposed online. Paper wallets use printed QR codes or private keys. | Highest level of security against online attacks. | Inconvenient for frequent transactions. Loss or damage to the physical storage medium results in irreversible loss of funds. Susceptible to physical theft or destruction. |
| Hardware Wallet (e.g., Ledger Nano S, Trezor) | Secure element chip, PIN protection, passphrase protection, often includes multi-signature support. Private keys are stored and processed on a tamper-resistant device. | High level of security, combines convenience with robust protection against online threats. Relatively user-friendly. | More expensive than software wallets, potential for device failure or loss. Requires careful handling and understanding of the device’s security features. |
Security Mechanisms in Cryptocurrency Wallets
Several key security mechanisms are employed across different wallet types. Understanding these mechanisms is critical for effective security.Multi-signature support requires multiple approvals before a transaction can be executed. This significantly reduces the risk of unauthorized access, even if one private key is compromised. For example, a 2-of-3 multi-signature setup needs two out of three key holders to approve a transaction.Seed phrases (also known as recovery phrases or mnemonic phrases) are a list of words that act as a backup for your private keys.
If your wallet is lost or compromised, your seed phrase allows you to restore access to your funds. It’s crucial to keep your seed phrase secure and offline, ideally in a physical location separate from your wallet.Encryption methods, such as Advanced Encryption Standard (AES), are used to protect your private keys and other sensitive data within the wallet. AES-256 is a widely used standard, offering a strong level of encryption.
However, the effectiveness of encryption depends on the overall security of the wallet and the user’s practices.
Risks Associated with Different Wallet Types
Each wallet type presents unique risks.Hot wallets are susceptible to malware, phishing attacks, and keyloggers, which can steal your private keys or seed phrase. For instance, a user might download a malicious software update that compromises their wallet’s security. Phishing attacks can trick users into revealing their credentials.Cold wallets face the risk of physical loss or damage, rendering your funds inaccessible.
Discover how Is ZetaChain a good investment for long-term growth? has transformed methods in this topic.
For example, a fire could destroy a paper wallet containing crucial information. Physical theft is another significant concern.Hardware wallets can be lost or stolen, but their tamper-resistant design offers a significant layer of protection against many attacks. However, vulnerabilities in the device’s firmware or the user’s handling practices could still compromise security. A user might accidentally reveal their PIN, or a firmware vulnerability could allow attackers to extract private keys.
Security Features within Wallets
Cryptocurrency wallets, whether software or hardware, incorporate a range of security features to protect your digital assets. The level of security offered varies depending on the wallet type and its specific implementation. Understanding these features is crucial for safeguarding your investments. This section will explore the security measures employed by popular wallets and delve into the mechanics of two-factor authentication.
Different wallets offer varying levels of security, combining software and hardware elements. Hardware wallets, for instance, offer significantly higher security compared to software wallets due to their offline nature. Software wallets, while convenient, rely heavily on strong passwords and other security features to protect user funds.
Security Features in Popular Wallets
Let’s examine the security features offered by some prominent cryptocurrency wallets. The features listed are not exhaustive, and specific implementations might differ slightly between wallet versions.
- Ledger (Hardware Wallet): Ledger wallets prioritize offline security. Key features include a secure element chip to protect private keys, a PIN code requirement for access, and firmware updates to patch vulnerabilities. They also often include recovery phrases for restoring access in case of device loss or damage.
- Trezor (Hardware Wallet): Similar to Ledger, Trezor wallets use a secure element chip to isolate private keys. They also incorporate features like passphrase protection (adding an extra layer of security to the seed phrase), a robust recovery process, and regular firmware updates.
- Exodus (Software Wallet): Exodus focuses on user-friendliness alongside security. While not as inherently secure as hardware wallets, Exodus employs features such as password protection, multi-signature transactions (requiring multiple approvals for a transaction), and optional integration with hardware wallets for enhanced security.
Two-Factor Authentication (2FA) in Cryptocurrency Wallets, Analyzing the security features of different cryptocurrency wallets.
Two-factor authentication (2FA) adds an extra layer of security by requiring two distinct forms of verification before granting access or authorizing a transaction. This significantly reduces the risk of unauthorized access, even if one authentication method is compromised. Typically, one factor is something you know (like a password), and the other is something you have (like a code from an authenticator app).
In cryptocurrency wallets, 2FA often involves a password (first factor) and a time-based one-time password (TOTP) generated by an authenticator app like Google Authenticator or Authy (second factor). When you attempt to log in or authorize a transaction, the wallet prompts you for both your password and the current code from your authenticator app. Without both, access is denied.
This makes it extremely difficult for attackers to gain access even if they obtain your password.
Comparison of 2FA Methods
Different 2FA methods offer varying levels of security and convenience. Here’s a comparison:
| 2FA Method | Strengths | Weaknesses | Security Level (Low-Medium-High) |
|---|---|---|---|
| Time-Based One-Time Password (TOTP) | Widely supported, relatively easy to use, good security if authenticator app is secure. | Relies on a smartphone or other device; vulnerable if the authenticator app is compromised or the device is lost. | Medium-High |
| Hardware Security Key (e.g., YubiKey) | Highly secure, resistant to phishing attacks, doesn’t rely on a smartphone. | Requires purchasing a physical key, can be less convenient than TOTP. | High |
| Email/SMS Verification | Simple to implement, widely available. | Vulnerable to SIM swapping and phishing attacks, less secure than TOTP or hardware keys. | Low-Medium |
| Biometric Authentication (Fingerprint/Facial Recognition) | Convenient, fast authentication. | Vulnerable to spoofing; security depends on the quality of the biometric sensor. | Medium |
Software and Hardware Wallet Security

Choosing between a software or hardware wallet significantly impacts your cryptocurrency’s security. Understanding the differences in their security protocols and best practices for each is crucial for protecting your digital assets. This section will delve into the security aspects of both types, highlighting key differences and essential security measures.
Software and hardware wallets employ different security approaches, each with its strengths and weaknesses. The level of security you need depends largely on the value of your cryptocurrency holdings and your personal risk tolerance. Let’s explore the specifics.
Software versus Hardware Wallet Security Protocols
The security protocols implemented in software and hardware wallets differ significantly. Hardware wallets offer a much higher level of security due to their isolated and physically protected environment. Here’s a comparison:
- Software Wallets: Primarily rely on software-based encryption and security measures. Vulnerable to malware, phishing attacks, and operating system compromises. Security depends heavily on the strength of the user’s password and the security of their device. They often store private keys on the user’s device, making them susceptible to theft if the device is compromised.
- Hardware Wallets: Employ a combination of hardware and software security measures. Private keys are generated and stored on a secure hardware element, isolated from the computer and internet. They typically use secure elements, similar to those found in credit cards, offering robust protection against malware and remote attacks. They often require a PIN or passphrase for access, adding an extra layer of security.
Importance of Regularly Updating Wallet Software
Regularly updating your wallet software is paramount for maintaining its security. Outdated software often contains known vulnerabilities that hackers can exploit. These vulnerabilities can allow attackers to gain access to your private keys and steal your cryptocurrency. Failing to update exposes your wallet to significant risks.
- Consequences of Using Outdated Versions: Using outdated software leaves your wallet susceptible to various attacks, including malware infections, phishing scams, and exploits targeting known vulnerabilities. This can lead to the complete loss of your cryptocurrency.
- Security Patches and Improvements: Updates often include critical security patches that address vulnerabilities discovered after the previous version’s release. They also frequently include performance improvements and new features designed to enhance security and user experience.
Best Practices for Securing Software and Hardware Wallets
Securing your cryptocurrency wallets requires a multi-faceted approach encompassing both physical and software security measures. Following best practices minimizes your risk of loss.
- Software Wallet Security: Use strong, unique passwords; enable two-factor authentication (2FA) wherever possible; regularly update your wallet software; install reputable antivirus and anti-malware software; be wary of phishing attempts and suspicious emails or websites; back up your wallet’s seed phrase securely offline (e.g., using a metal plate or a paper wallet stored in a safe).
- Hardware Wallet Security: Store your hardware wallet in a safe place, away from potential thieves; never connect your hardware wallet to untrusted computers or networks; always verify the device’s authenticity before using it; regularly update the firmware of your hardware wallet; use a strong PIN or passphrase; keep a secure backup of your recovery seed phrase (following the manufacturer’s recommendations for secure storage).
Ultimately, securing your cryptocurrency requires a multi-faceted approach. Choosing the right wallet is just the first step. By understanding the vulnerabilities associated with each type, implementing robust security measures like 2FA, and staying vigilant against phishing scams, you significantly reduce your risk of loss. Remember, regular updates, strong passwords, and secure backups are your best defense against cyber threats.
Staying informed and proactive is key to protecting your digital wealth.