Analyzing the long-term potential of blockchain technology. is crucial because this revolutionary technology is rapidly evolving, impacting various sectors. We’ll explore its scalability challenges, regulatory hurdles, economic implications, diverse applications, and inherent security features. Understanding these facets is key to predicting its future influence on our world.
This exploration delves into the technological advancements needed to overcome current limitations, analyzing different consensus mechanisms and Layer-2 solutions. We’ll examine how evolving regulations globally will shape blockchain’s growth and consider its potential to disrupt existing economic models and create new ones. Finally, we’ll assess its security, the importance of decentralization, and envision potential future applications across numerous industries.
Specific Use Cases and Applications
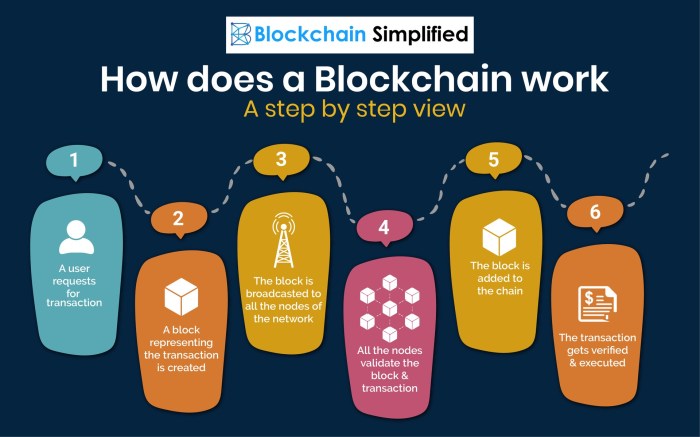
Blockchain technology, beyond the initial hype surrounding cryptocurrencies, offers a transformative potential across diverse sectors. Its decentralized, secure, and transparent nature is disrupting traditional business models and creating new opportunities for innovation. This section explores three key industries primed for significant blockchain-driven change, examining successful applications and comparing them to conventional approaches.
Blockchain in Supply Chain Management
Supply chain management is ripe for disruption by blockchain’s ability to enhance transparency and traceability. Traditional supply chains often suffer from a lack of visibility, making it difficult to track products and materials throughout their journey from origin to consumer. This can lead to inefficiencies, counterfeiting, and difficulty in identifying and resolving issues. Blockchain, however, provides a shared, immutable ledger that records every step of the process, offering real-time tracking and enhanced security.
A prime example is Walmart’s implementation of blockchain technology to track its food supply chain. By using blockchain to record information about the origin, handling, and transportation of food products, Walmart can quickly identify and address potential contamination issues, reducing response times and minimizing potential health risks. This significantly improves food safety and consumer trust. Another example is the use of blockchain in the diamond industry to ensure the ethical sourcing of diamonds, preventing the sale of conflict diamonds (“blood diamonds”).
Comparing blockchain solutions to traditional methods reveals several key advantages. Blockchain offers increased transparency and traceability, improved security through cryptographic hashing, and reduced costs associated with manual tracking and verification. However, scalability remains a challenge for some blockchain platforms, and integrating blockchain into existing systems can require significant investment and expertise.
Blockchain in Healthcare
The healthcare industry is grappling with issues of data security, interoperability, and patient privacy. Blockchain’s decentralized and secure nature offers a promising solution. Traditional methods often involve centralized databases that are vulnerable to breaches and lack seamless data sharing between different healthcare providers.
One successful application is the use of blockchain to securely store and manage patient medical records. A blockchain-based system allows patients to control access to their data, sharing it only with authorized healthcare providers. This improves patient privacy and empowers individuals to manage their health information more effectively. Furthermore, blockchain can streamline the process of clinical trials by securely storing and sharing data among researchers, accelerating the development of new treatments and medications.
Blockchain solutions offer enhanced security, improved data interoperability, and increased patient control over their medical information. However, the regulatory landscape surrounding healthcare data is complex, and implementing blockchain systems requires careful consideration of compliance issues. Moreover, the integration of blockchain into existing healthcare infrastructure can be a challenging and costly undertaking.
Blockchain in Digital Identity Management
The management of digital identities is a crucial aspect of online security and privacy. Traditional methods often rely on centralized systems that are vulnerable to hacking and data breaches. Blockchain technology offers a decentralized and secure alternative.
Several projects are exploring the use of blockchain to create secure and verifiable digital identities. These systems allow individuals to control their own identity data, granting access only to authorized parties. This enhances privacy and reduces the risk of identity theft. Furthermore, blockchain can simplify the process of verifying identities for various purposes, such as accessing online services or completing financial transactions.
Blockchain-based digital identity systems offer enhanced security, improved privacy, and greater control for individuals over their own data. However, scalability and interoperability remain challenges, and widespread adoption requires the development of robust standards and protocols. Moreover, there are concerns about the potential for misuse of blockchain-based identity systems.
Blockchain Platform Comparison, Analyzing the long-term potential of blockchain technology.
| Platform | Scalability | Security | Suitable Applications |
|---|---|---|---|
| Ethereum | Moderate | High | Supply chain, Healthcare (smart contracts), Decentralized Applications (dApps) |
| Hyperledger Fabric | High | High | Supply chain, Healthcare (data management), Enterprise solutions |
| Corda | Moderate | High | Financial transactions, Supply chain (private transactions) |
| R3 Corda | Moderate | High | Financial services, Trade finance |
A Future Integrated with Blockchain
Imagine a future where every transaction, from purchasing groceries to accessing healthcare services, is secured and transparently recorded on a blockchain. Individuals possess self-sovereign digital identities, granting them complete control over their personal data. Supply chains are fully traceable, ensuring product authenticity and ethical sourcing. Healthcare systems seamlessly share patient information, improving care coordination and reducing medical errors.
This isn’t science fiction; it’s a vision of a future where blockchain technology underpins a more secure, efficient, and trustworthy society. This future scenario emphasizes the seamless integration of blockchain into everyday life, automating processes and enhancing trust across various sectors. It is a world where data privacy and security are paramount, and individuals have greater control over their digital identities and information.
The everyday experience would be more secure, transparent, and efficient due to the underlying blockchain infrastructure.
Security and Decentralization: Analyzing The Long-term Potential Of Blockchain Technology.
Blockchain technology boasts inherent security features stemming from its decentralized and cryptographic nature. However, no system is impenetrable, and blockchain networks are susceptible to various attacks, the effectiveness of which depends on the specific implementation and the chosen consensus mechanism. Understanding these vulnerabilities is crucial for building robust and secure blockchain applications.Blockchain security relies heavily on cryptography, ensuring data integrity and user authentication.
Transactions are cryptographically hashed and linked together, forming an immutable chain. Altering a single block requires recalculating all subsequent hashes, a computationally infeasible task for large blockchains. This immutability is a core strength, but it’s not absolute; vulnerabilities can still exist in the smart contracts running on the blockchain or in the implementation of the cryptographic algorithms.
Comparison of Consensus Mechanisms and Their Security
Different consensus mechanisms offer varying levels of security and efficiency. Proof-of-Work (PoW), famously used by Bitcoin, relies on miners competing to solve complex cryptographic puzzles. The energy-intensive nature of PoW makes it computationally expensive for attackers to alter the blockchain. However, it’s not without its flaws; 51% attacks, where a single entity controls over half the network’s hashing power, remain a theoretical threat, though practically difficult to achieve for established networks like Bitcoin.
Proof-of-Stake (PoS), used by Ethereum and many other blockchains, is generally considered more energy-efficient. Validators are selected based on the amount of cryptocurrency they stake, incentivizing them to act honestly. While PoS is less energy-intensive, it is still susceptible to attacks, such as long-range attacks or stake-pooling vulnerabilities where a group of validators collude to control the network.
Other mechanisms, like Delegated Proof-of-Stake (DPoS) and Practical Byzantine Fault Tolerance (PBFT), present their own trade-offs between security, scalability, and energy consumption. The choice of consensus mechanism significantly impacts the overall security posture of a blockchain network.
Decentralization and Blockchain Integrity
Decentralization is the cornerstone of blockchain’s security and resilience. It distributes trust across a network of nodes, eliminating single points of failure and making the system resistant to censorship and manipulation. If one node or a small group of nodes fails, the network continues to function. This contrasts sharply with centralized systems, where a single point of failure can bring down the entire system.
The decentralized nature makes it incredibly difficult for a single entity to control or alter the blockchain’s data. However, a sufficiently large and coordinated attack, perhaps involving compromised nodes, could still pose a threat.
Threats to Decentralization
While the ideal of complete decentralization is appealing, several factors can threaten its realization. One major threat is the concentration of mining or staking power in the hands of a few large entities. This can lead to a less decentralized network, making it more vulnerable to attacks. Another threat is the rise of “permissioned” blockchains, where access and participation are restricted, thus compromising the open and distributed nature of the technology.
Furthermore, regulatory pressures from governments could inadvertently lead to centralization by imposing strict compliance requirements that disproportionately affect smaller nodes. Finally, the development of sophisticated attack vectors, such as sybil attacks where a single entity controls many nodes, also poses a continuous challenge to maintaining a truly decentralized network.
Best Practices for Securing Blockchain Applications and Networks
Maintaining the security of blockchain applications and networks requires a multifaceted approach. Here are some best practices:
- Employ robust cryptographic techniques: Use strong encryption algorithms and key management practices to protect sensitive data.
- Regular security audits: Conduct frequent audits of smart contracts and blockchain infrastructure to identify and address vulnerabilities.
- Diversify node infrastructure: Distribute nodes across geographically diverse locations to enhance resilience against attacks.
- Implement robust access controls: Control access to nodes and applications using secure authentication and authorization mechanisms.
- Monitor network activity: Continuously monitor network activity for suspicious behavior, such as unusually high transaction volumes or attempts to manipulate the blockchain.
- Stay updated with security patches: Regularly update software and firmware to address known vulnerabilities.
- Promote diversity in consensus mechanisms: Explore and implement alternative consensus mechanisms to reduce reliance on a single point of failure.
- Develop and implement comprehensive incident response plans: Prepare for potential security incidents and establish clear procedures for responding to attacks.
Blockchain technology holds immense long-term potential, but its success hinges on overcoming significant technological, regulatory, and security challenges. While hurdles remain, the potential for increased transparency, efficiency, and economic disruption across various sectors is undeniable. Continued innovation and thoughtful regulation are crucial for unlocking blockchain’s transformative power and shaping a future where its benefits are widely accessible and secure.
Find out further about the benefits of What are the different types of consensus mechanisms used in blockchain technology? that can provide significant benefits.
Remember to click Is ZetaChain a good investment for long-term growth? to understand more comprehensive aspects of the Is ZetaChain a good investment for long-term growth? topic.