A beginner’s guide to understanding blockchain technology and its applications. This guide demystifies the often-confusing world of blockchain, explaining its core concepts, applications, and future potential in clear, simple terms. We’ll explore how this revolutionary technology works, from its basic building blocks to its diverse uses beyond cryptocurrencies, such as supply chain management and secure data storage in healthcare.
Get ready to unravel the secrets of this transformative technology!
We’ll cover the fundamental components of a blockchain, including blocks, chains, and the crucial role of cryptography. You’ll learn about different types of blockchain networks – public, private, and permissioned – and discover how they are used in various real-world scenarios. We’ll also explore the relationship between blockchain and cryptocurrencies, examining different types of cryptocurrencies and their functionalities. Finally, we’ll look at the future of blockchain, considering both its potential and the challenges it faces.
Introduction to Blockchain Technology
Imagine a digital ledger that’s shared publicly and is virtually impossible to tamper with. That’s the essence of blockchain technology. It’s a revolutionary way to record and verify transactions, and it’s not just about cryptocurrencies like Bitcoin; it has the potential to transform many industries. This technology relies on a distributed network of computers to maintain and update this shared ledger, ensuring transparency and security.Blockchain works by grouping transactions into “blocks.” Once a block is full, it’s added to the chain, creating a chronological record.
Each block is linked to the previous one using cryptography, making it incredibly difficult to alter any past transaction without detection. Think of it like a tamper-evident seal on a package; if someone tries to open it, it’s immediately obvious. This interconnectedness of blocks forms the “chain,” hence the name blockchain.
A Simple Analogy: The Shared Google Doc
Imagine a shared Google Doc that everyone in a group can access and edit. However, every time someone makes a change, that change is recorded, timestamped, and visible to everyone. Furthermore, no single person can delete or alter past entries without everyone else noticing. This shared, transparent, and immutable record is similar to how a blockchain functions. While a Google Doc can be deleted by its owner, a blockchain, due to its distributed nature and cryptographic security, is far more resistant to such alterations.
A Brief History of Blockchain
The foundational concept of blockchain technology emerged in 1991 with Stuart Haber and W. Scott Stornetta’s work on a system for digitally timestamping documents to prevent tampering. However, it wasn’t until the release of Bitcoin’s whitepaper by Satoshi Nakamoto in 2008 that blockchain gained widespread attention. Bitcoin implemented the blockchain to securely manage its cryptocurrency transactions. Since then, the technology has evolved significantly, expanding beyond cryptocurrencies to encompass diverse applications across various sectors.
Early blockchain implementations were primarily focused on cryptocurrencies, but now we see its use in supply chain management, healthcare, voting systems, and many other areas.
Core Components of Blockchain: A Beginner’s Guide To Understanding Blockchain Technology And Its Applications.
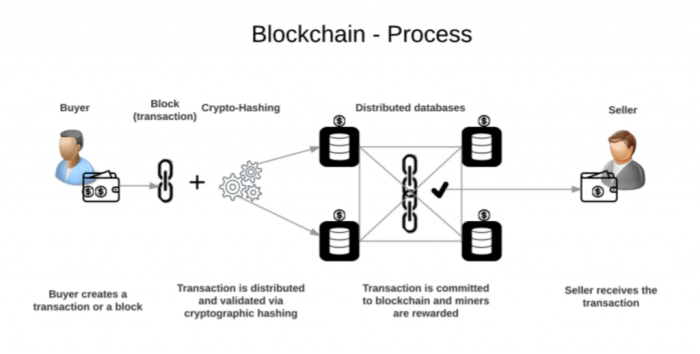
Think of a blockchain like a digital ledger that’s shared publicly and securely. This ledger isn’t stored in one place but is distributed across many computers, making it incredibly resistant to tampering. Its core strength comes from three key components: blocks, chains, and cryptographic hashes. Let’s break them down.
At its heart, a blockchain is a chain of blocks. Each block contains a set of validated transactions. These transactions could be anything from cryptocurrency transfers to supply chain data. The blocks are linked together chronologically, creating a permanent and transparent record of events.
Blocks
Blocks are the fundamental building blocks of a blockchain. Each block contains a specific amount of data, typically a batch of transactions. Crucially, a block also includes a unique identifier called a hash, and a reference to the hash of the previous block. This linking creates the chain. Imagine each block as a page in a ledger, and the reference to the previous block as a page number linking it to the previous page.
This structure makes it extremely difficult to alter past transactions without detection. A block’s capacity varies depending on the specific blockchain’s design, but once full, a new block is added to the chain.
Chains
The chain aspect is what gives blockchain its strength. Blocks are linked together chronologically, creating a sequence of records. Each block’s hash is a unique fingerprint, and it’s computationally infeasible to change a block’s contents without altering its hash. Because the hash of a block is linked to the hash of the previous block, any change in a previous block would ripple through the entire chain, causing a mismatch and immediately flagging the alteration.
This interconnectedness provides a high level of integrity and security.
Hashes
Cryptographic hashes are essential for blockchain security. A hash is a one-way function that takes an input (in this case, the data within a block) and produces a unique, fixed-size string of characters. Even a tiny change in the input data will result in a completely different hash. This property ensures data integrity. If someone tries to alter the data in a block, the resulting hash will be different, immediately revealing the tampering.
The use of cryptographic hashes provides a tamper-evident system. For example, the SHA-256 algorithm is commonly used to generate hashes in many blockchains.
Adding a New Block
Adding a new block to the blockchain is a multi-step process involving verification and consensus mechanisms. First, transactions are collected and grouped together. Then, these transactions are bundled into a new block. Next, this block’s data is hashed, and the hash of the previous block is included. Finally, the new block is added to the chain only after it’s verified by a majority of network participants (miners or validators), ensuring the integrity of the entire chain.
This verification process is what prevents fraudulent additions or alterations to the blockchain.
The Role of Cryptography
Cryptography is the backbone of blockchain security. It’s used not only in generating hashes but also in securing transactions and verifying identities. Public-key cryptography is often employed, allowing users to have a public key (for receiving transactions) and a private key (for authorizing transactions). This ensures that only the rightful owner can spend their cryptocurrencies or make changes.
Digital signatures, another cryptographic tool, provide authentication and non-repudiation, meaning users cannot deny their transactions. The combined use of these cryptographic techniques makes blockchain highly secure and resistant to fraud.
Types of Blockchain Networks
So far, we’ve covered the basics of blockchain. Now let’s dive into the different types of blockchain networks, each with its own unique characteristics and applications. Understanding these differences is crucial for grasping the versatility of this technology. The primary distinction lies in who can participate in the network and how transactions are validated.
There are three main types of blockchain networks: public, private, and permissioned (sometimes called consortium). Each offers a different balance between decentralization, security, and control.
Public Blockchains
Public blockchains are open and decentralized. Anyone can participate, view transactions, and contribute to the network’s security by validating transactions (mining). This open nature promotes transparency and trust, as all participants have equal access to the data. However, this openness also comes with some drawbacks.
The decentralized nature makes public blockchains resistant to censorship and single points of failure. However, this also means slower transaction speeds and higher energy consumption compared to other types of blockchains.
Private Blockchains
Private blockchains, in contrast, are centralized and controlled by a single entity or organization. Only authorized users can participate, view transactions, and validate them. This centralized control allows for faster transaction speeds and greater privacy, but it also sacrifices the decentralization and transparency that are hallmarks of public blockchains.
Because a single entity manages a private blockchain, it is more susceptible to manipulation and single points of failure. However, this control also allows for greater efficiency and customization.
Permissioned Blockchains
Permissioned blockchains, also known as consortium blockchains, represent a middle ground between public and private networks. Access to the network is restricted to a pre-defined group of participants, who are granted permission to join. This allows for a balance between decentralization and control. The level of decentralization can vary widely depending on the specific design of the permissioned blockchain.
Permissioned blockchains offer a good compromise between the benefits of public and private blockchains, allowing for greater control while maintaining a degree of decentralization and transparency among the authorized participants. However, the limited participation may restrict its scalability and widespread adoption.
Comparison of Blockchain Network Types
| Type | Description | Advantages | Disadvantages |
|---|---|---|---|
| Public | Open, decentralized, anyone can participate. | Transparent, secure, censorship-resistant. | Slow transaction speeds, high energy consumption, scalability challenges. |
| Private | Centralized, controlled by a single entity. | Fast transaction speeds, high privacy, easy to manage. | Less secure, susceptible to single points of failure, lack of transparency. |
| Permissioned | Restricted access, controlled by a group of participants. | Balance between decentralization and control, improved security compared to private, faster than public. | Limited participation, potential for collusion among participants. |
Understanding Cryptocurrencies

Cryptocurrencies are digital or virtual currencies designed to work as a medium of exchange. They use cryptography to secure and verify transactions as well as to control the creation of new units of a particular cryptocurrency. Crucially, their operation relies heavily on blockchain technology, forming a symbiotic relationship.Cryptocurrencies leverage blockchain technology to record and verify transactions in a decentralized and transparent manner.
Each transaction is added as a block to the blockchain, creating a permanent and tamper-proof record. This eliminates the need for a central authority like a bank, making the system more secure and resistant to censorship.
The Relationship Between Blockchain and Cryptocurrencies
Blockchain provides the foundational infrastructure for cryptocurrencies. It’s the distributed ledger that tracks every cryptocurrency transaction, ensuring transparency and security. Without blockchain’s decentralized and immutable nature, cryptocurrencies wouldn’t be able to function as intended. The blockchain acts as a public, shared database, preventing double-spending and ensuring the integrity of the currency. Imagine trying to manage a currency without a reliable record-keeping system – it would be chaotic and easily manipulated.
Blockchain solves this problem by providing that reliable and secure system.
How Cryptocurrencies Use Blockchain Technology
Cryptocurrencies utilize blockchain’s core features to operate. When a transaction occurs (e.g., sending Bitcoin from one wallet to another), the transaction details are broadcast to the network. Miners (or validators in proof-of-stake systems) then verify the transaction, bundle it with other transactions into a block, and add it to the blockchain. This process requires significant computational power (in proof-of-work systems) or staked cryptocurrency (in proof-of-stake systems), incentivizing participants to maintain the integrity of the system.
The cryptographic hashing algorithms ensure the security and immutability of the blockchain, making it extremely difficult to alter past transactions.
Types of Cryptocurrencies and Their Functionalities
The cryptocurrency landscape is diverse, with thousands of different cryptocurrencies, each with its own unique features and functionalities. Some key examples include:
- Bitcoin (BTC): The first and most well-known cryptocurrency, primarily used as a store of value and a medium of exchange.
- Ethereum (ETH): A platform for decentralized applications (dApps) and smart contracts, enabling the creation of new cryptocurrencies and decentralized finance (DeFi) applications.
- Stablecoins (e.g., Tether (USDT), USD Coin (USDC)): Cryptocurrencies pegged to a stable asset like the US dollar, aiming to minimize price volatility.
- Privacy Coins (e.g., Monero (XMR), Zcash (ZEC)): Cryptocurrencies designed to enhance user privacy by obscuring transaction details.
These are just a few examples, and the functionalities of cryptocurrencies are constantly evolving. Some are designed for payments, others for decentralized governance, and still others for specific niche applications within DeFi or the metaverse. The variety reflects the innovative potential of blockchain technology and its capacity to support a wide range of use cases.
Blockchain Applications Beyond Cryptocurrencies
Blockchain technology, while famously associated with cryptocurrencies, offers a much broader range of applications across various industries. Its inherent security, transparency, and immutability make it a powerful tool for streamlining processes and enhancing trust in diverse systems. Let’s explore some key examples.
Blockchain in Supply Chain Management
Implementing blockchain in supply chain management revolutionizes tracking and verification of goods throughout their journey, from origin to consumer. This enhanced transparency improves efficiency, reduces fraud, and boosts consumer confidence. Imagine a scenario where every step of a product’s journey – from raw material sourcing to manufacturing, distribution, and retail – is recorded on a shared, immutable ledger.
This creates an auditable trail that is accessible to all authorized participants.
Below is a flowchart illustrating a simplified blockchain-based supply chain process for coffee beans:
Flowchart: Blockchain in Coffee Bean Supply Chain
Step 1: Farmer harvests coffee beans and registers the harvest details (quantity, quality, location) on the blockchain.
Step 2: Beans are transported to a processing facility. The transporter updates the blockchain with shipment details (tracking number, date, location).
Step 3: Processing facility verifies the beans, records processing details (roasting, packaging), and updates the blockchain.
Step 4: Packaged beans are shipped to a distributor. The distributor updates the blockchain with shipment details.
Step 5: Distributor ships to retailer. Retailer updates the blockchain.
Step 6: Retailer sells beans to consumer. The entire history is available to the consumer via a unique product code, verifying authenticity and origin.
Blockchain in Healthcare for Secure Data Management
Blockchain’s secure and decentralized nature makes it ideally suited for managing sensitive healthcare data. The potential for improved patient privacy, streamlined data sharing, and enhanced interoperability is significant.
Here are some key benefits of using blockchain in healthcare:
- Enhanced Patient Privacy: Patients have greater control over their data, choosing who can access it and for what purposes.
- Improved Data Security: Blockchain’s cryptographic security protects medical records from unauthorized access and tampering.
- Streamlined Data Sharing: Secure and efficient sharing of medical records between healthcare providers improves patient care coordination.
- Reduced Medical Errors: Accurate and readily available medical history reduces the risk of medication errors and other medical mishaps.
- Increased Transparency and Trust: A transparent and auditable system builds trust between patients and healthcare providers.
Blockchain in Voting Systems and Digital Identity Management
Blockchain technology offers potential solutions for enhancing the security and transparency of voting systems and managing digital identities. For voting, a blockchain-based system could record votes securely and immutably, reducing the risk of fraud and manipulation. For digital identity, a blockchain-based system could provide individuals with greater control over their personal data, while enabling secure and verifiable identity verification across various platforms.
For example, Estonia has made significant strides in leveraging blockchain for digital identity, offering citizens a secure and convenient way to access various government and private services online. Similarly, several countries are exploring blockchain-based voting solutions to enhance the integrity of elections.
The Future of Blockchain Technology
Predicting the future is always a risky business, but based on current trends and advancements, we can make some educated guesses about where blockchain technology is headed. It’s poised for significant growth, but also faces hurdles that need to be overcome for widespread adoption. This section explores both the exciting possibilities and the potential challenges.Blockchain technology is constantly evolving, with new innovations emerging regularly.
These advancements promise to enhance its efficiency, scalability, and security, leading to broader applications across various sectors. However, challenges related to regulation, interoperability, and energy consumption remain significant obstacles to overcome.
Potential Future Developments and Advancements
Several key areas are ripe for significant advancements. Improved scalability solutions are crucial to handle the increasing transaction volume expected as blockchain adoption grows. Enhanced privacy features are also vital, particularly for sensitive data applications. Furthermore, the integration of artificial intelligence (AI) and machine learning (ML) can automate processes and optimize blockchain networks, leading to more efficient and secure systems.
Finally, the development of more user-friendly interfaces will be essential for wider mainstream adoption.
Potential Challenges and Limitations of Widespread Blockchain Adoption
Despite its potential, widespread blockchain adoption faces several significant challenges. Regulatory uncertainty is a major concern, as governments grapple with how to regulate this new technology. Lack of interoperability between different blockchain networks hinders seamless data exchange and collaboration. The high energy consumption of some blockchain networks, particularly proof-of-work systems like Bitcoin, raises environmental concerns. Furthermore, the complexity of blockchain technology can be a barrier to entry for many users, limiting its accessibility.
Finally, security concerns, although generally low, still exist, and require constant vigilance and improvement.
Future Trends in Blockchain Technology, A beginner’s guide to understanding blockchain technology and its applications.
| Trend | Description |
|---|---|
| Increased Scalability | Solutions like sharding and layer-2 scaling will address the limitations of current blockchain networks, allowing them to handle a much larger volume of transactions per second. This is crucial for widespread adoption in applications like supply chain management and financial transactions, where high throughput is essential. For example, Ethereum’s move towards sharding is a prime example of this trend. |
| Enhanced Privacy | Developments in zero-knowledge proofs and other privacy-enhancing technologies will allow for transactions and data storage with increased confidentiality. This is particularly important for applications dealing with sensitive personal information or financial data, enabling greater trust and security. Examples include projects like Zcash and privacy coins. |
| Integration with AI and ML | The combination of blockchain’s immutability and AI’s analytical capabilities will create powerful tools for fraud detection, risk management, and process automation. This will lead to more efficient and secure systems across various industries. For example, AI could be used to analyze blockchain data to identify potentially fraudulent transactions in real-time. |
| Improved User Experience | Simpler interfaces and user-friendly tools will make blockchain technology more accessible to a wider audience. This will reduce the technical barrier to entry and encourage greater adoption. This could involve the development of intuitive wallets and applications that require minimal technical knowledge to use. |
| Regulatory Clarity | As governments develop clearer regulatory frameworks, the uncertainty surrounding blockchain will decrease, encouraging investment and innovation. This will create a more stable and predictable environment for blockchain businesses to operate in. The development of specific blockchain regulations in various jurisdictions is a crucial step in this process. |
Security and Privacy Considerations
Blockchain technology, while revolutionary, isn’t immune to security risks or privacy concerns. Understanding these aspects is crucial for anyone engaging with blockchain-based systems, whether it’s using cryptocurrencies or exploring other applications. This section will explore the security mechanisms in place, the privacy implications, and potential vulnerabilities.
Blockchain Security Mechanisms
Blockchain’s inherent security stems from several key features. Cryptography plays a central role, securing transactions and data integrity. Each block is cryptographically linked to the previous one, creating an immutable chain. This makes altering past transactions extremely difficult, requiring the manipulation of a significant portion of the network. Furthermore, the decentralized nature of many blockchains distributes the data across numerous nodes, making it highly resilient to single points of failure or attacks.
Consensus mechanisms, like Proof-of-Work or Proof-of-Stake, ensure that new blocks are added legitimately, requiring agreement from a majority of network participants. These mechanisms, while not perfect, create a robust and secure system compared to traditional centralized databases.
Privacy Implications of Blockchain
While often touted for its transparency, blockchain’s inherent openness presents privacy challenges. Many public blockchains record all transactions publicly and permanently. This means anyone can view transaction details, including sender and receiver addresses, although not necessarily their real-world identities. This lack of anonymity can be a concern for users who value privacy. However, advancements like zero-knowledge proofs and privacy coins are emerging to address these issues.
Zero-knowledge proofs allow verification of information without revealing the underlying data. Privacy coins, such as Monero and Zcash, employ techniques to obfuscate transaction details, enhancing user anonymity.
Potential Vulnerabilities and Risks
Despite its robust security, blockchain systems are not invulnerable. 51% attacks, where a single entity controls more than half of the network’s computing power, represent a significant threat. Such an attack could allow malicious actors to reverse transactions or double-spend cryptocurrencies. Smart contract vulnerabilities are another concern. Bugs in the code of smart contracts can be exploited to drain funds or cause other unintended consequences, as seen in several high-profile incidents.
Quantum computing also poses a long-term threat, as sufficiently powerful quantum computers could potentially break the cryptographic algorithms currently securing blockchain networks. Finally, exchanges and custodial wallets, while not directly part of the blockchain, represent a point of vulnerability. Security breaches at these entities can result in the loss of user funds.
Understanding blockchain technology is no longer a niche pursuit; it’s becoming increasingly relevant in our interconnected world. This guide has provided a foundational understanding of blockchain’s mechanics, its diverse applications beyond cryptocurrencies, and its potential to reshape various industries. By grasping the core concepts and applications explored here, you’re well-equipped to navigate the exciting landscape of blockchain technology and its transformative power.
As this technology continues to evolve, remember that staying informed and curious is key to understanding its future impact.