Exploring the use of blockchain technology in digital identity verification. – Exploring the use of blockchain technology in digital identity verification, we’ll dive into how this innovative technology is revolutionizing how we prove who we are online. Forget clunky, insecure systems; blockchain offers a potential solution for creating secure, transparent, and user-controlled digital identities. We’ll examine its core principles, explore different architectures, and discuss the vital security and privacy considerations involved.
Get ready to understand the potential and challenges of this transformative technology.
This exploration will cover the fundamental aspects of blockchain and its application to digital identity, including the comparison of various consensus mechanisms, the design of secure blockchain architectures, and the crucial role of smart contracts. We’ll also delve into the security and privacy implications, exploring potential vulnerabilities and mitigation strategies, and addressing relevant regulatory compliance challenges. Real-world applications across different sectors will be examined, alongside discussions on interoperability, scalability, and future trends in this rapidly evolving field.
Blockchain Architectures for Digital Identity
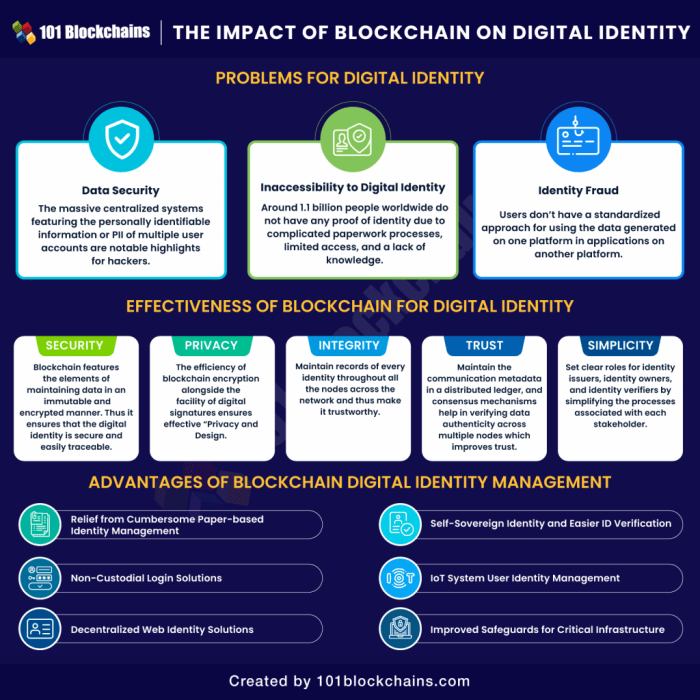
Designing a secure and efficient system for digital identity verification using blockchain requires careful consideration of several architectural elements. A well-structured blockchain architecture can enhance privacy, security, and interoperability, leading to a more trustworthy and user-friendly digital identity ecosystem. This section explores key aspects of such an architecture.
Data Storage and Retrieval
Secure and efficient data storage is paramount. Instead of storing personally identifiable information (PII) directly on the blockchain (due to scalability and privacy concerns), we can use a decentralized identifier (DID) system. Each individual’s DID acts as a unique key, pointing to their verifiable credentials stored off-chain, perhaps in an encrypted format within a decentralized storage solution like IPFS.
The blockchain only stores cryptographic hashes of these credentials and metadata about the DID’s creation and updates, ensuring immutability and auditability of identity claims without compromising privacy. This approach allows for scalability and maintains the integrity of the system. Access to the off-chain data is controlled by the individual through cryptographic keys associated with their DID.
Access Control Mechanisms
Robust access control is crucial to prevent unauthorized access to sensitive identity data. This can be achieved through a combination of techniques. Role-based access control (RBAC) can define different permission levels for various stakeholders (individuals, verifiers, and issuers). Zero-knowledge proofs (ZKPs) allow individuals to prove their identity without revealing the underlying data, enhancing privacy. Furthermore, cryptographic signatures tied to DIDs ensure the authenticity and integrity of transactions related to identity verification.
Access is granted based on pre-defined rules encoded within smart contracts, providing an automated and secure control mechanism.
Transaction Management
Efficient transaction management is key to a smooth and scalable system. The use of consensus mechanisms, such as Practical Byzantine Fault Tolerance (PBFT) in permissioned blockchains or Proof-of-Stake (PoS) in permissionless systems, ensures the integrity and security of transactions. Transaction fees, if any, should be carefully considered to avoid hindering adoption. The system should be designed to handle a large volume of transactions efficiently, possibly employing sharding or other scaling solutions.
Each transaction related to identity verification would be recorded on the blockchain, providing an immutable audit trail.
Permissioned vs. Permissionless Blockchain Approaches
Permissioned blockchains offer greater control and privacy but may suffer from reduced decentralization. In a permissioned system, only authorized participants (e.g., government agencies, identity providers) can participate in the network. This allows for tighter governance and better enforcement of access control policies, which is suitable for sensitive identity data. Permissionless blockchains, on the other hand, are more decentralized and transparent, but they may have security and privacy challenges.
Anyone can participate, potentially leading to vulnerabilities and difficulties in enforcing access control. The choice between these approaches depends on the specific requirements of the system and the level of trust and transparency needed. A hybrid approach might be the optimal solution, combining the strengths of both permissioned and permissionless models.
Smart Contracts for Automating Identity Verification
Smart contracts automate and streamline identity verification processes. They act as trusted intermediaries, enforcing pre-defined rules and conditions for identity verification. For example, a smart contract can verify the authenticity of a digital credential presented by an individual, ensuring that the credential has been issued by a trusted authority and has not been tampered with. This automation reduces the need for manual intervention, improving efficiency and reducing the risk of errors.
Sample Smart Contract (Pseudocode)
“`function verifyCredential(credentialHash, issuerAddress, userAddress) // Check if the issuer is authorized. if (!isAuthorizedIssuer(issuerAddress)) revert(“Unauthorized issuer”); // Verify the credential’s integrity using its hash. if (!verifyHash(credentialHash, getCredentialData(userAddress))) revert(“Invalid credential”); // Update user’s identity status. updateUserStatus(userAddress, “verified”); return true;“`
Security and Privacy Considerations: Exploring The Use Of Blockchain Technology In Digital Identity Verification.
Implementing blockchain for digital identity verification presents unique security and privacy challenges. While blockchain’s inherent immutability and decentralization offer advantages, careful consideration of potential vulnerabilities and robust mitigation strategies are crucial for building a trustworthy system. Balancing the benefits of secure identity management with the protection of sensitive personal data is paramount.
Security Implications of Storing Sensitive Data on a Blockchain, Exploring the use of blockchain technology in digital identity verification.
Storing sensitive identity data directly on a blockchain introduces several security risks. The immutability of blockchain, while a strength in terms of data integrity, also means that any erroneous or malicious data entered is permanently recorded. Smart contract vulnerabilities could allow unauthorized access or modification of data. Furthermore, the public nature of many blockchains means that even anonymized or hashed data might be susceptible to sophisticated analysis techniques leading to potential re-identification.
Mitigation strategies include employing robust access control mechanisms, utilizing zero-knowledge proofs to verify identity without revealing underlying data, and implementing multi-signature schemes to authorize sensitive transactions. Careful consideration of the type of data stored on-chain versus off-chain is also vital, minimizing the on-chain footprint to only essential, non-sensitive data.
Best Practices for Ensuring User Privacy and Data Protection
Protecting user privacy in a blockchain-based digital identity system requires a multi-faceted approach. Data minimization is key – only the absolutely necessary data should be stored. Techniques like differential privacy can add noise to data without compromising its utility for verification purposes. Homomorphic encryption allows computations on encrypted data without decryption, enhancing privacy during processing. Strong cryptographic techniques, including robust hashing algorithms and encryption methods, are essential for securing data both in transit and at rest.
Regular security audits and penetration testing are vital to identify and address potential vulnerabilities proactively. Furthermore, a clear and transparent privacy policy outlining data handling practices is crucial for building user trust. Implementing user consent mechanisms and providing users with control over their data are also essential aspects of a privacy-respecting system.
Regulatory and Compliance Challenges
Navigating the complex regulatory landscape surrounding data privacy and security is a significant challenge for blockchain-based digital identity systems. Regulations like GDPR (General Data Protection Regulation) in Europe and CCPA (California Consumer Privacy Act) in the US impose stringent requirements on data collection, storage, processing, and sharing. Compliance necessitates careful consideration of data subject rights, data breach notification procedures, and the implementation of appropriate technical and organizational measures.
International data transfer regulations further complicate the picture, particularly for systems operating across borders.
| Regulation | Key Provisions Relevant to Digital Identity | Data Subject Rights | Enforcement |
|---|---|---|---|
| GDPR | Data minimization, purpose limitation, data security, accountability, cross-border data transfers | Right to access, rectification, erasure, restriction of processing, data portability, objection | High fines for non-compliance |
| CCPA | Data collection disclosure, consumer rights regarding data access, deletion, and opt-out | Right to know, delete, and opt-out of data sale | Civil penalties for violations |
| Other Regional Regulations (e.g., LGPD in Brazil, PIPEDA in Canada) | Varying requirements regarding data protection, consent, and cross-border data transfers. Often mirror aspects of GDPR. | Rights vary by region, but often include access, correction, and deletion. | Enforcement mechanisms vary by region. |
Use Cases and Applications

Blockchain technology offers a revolutionary approach to digital identity verification, promising enhanced security and user control. Its decentralized and immutable nature makes it particularly attractive for managing sensitive personal data across various sectors. Let’s explore some practical applications and their implications.
Several industries are already exploring or implementing blockchain-based digital identity solutions. The benefits and drawbacks vary depending on the specific context and implementation. Understanding these nuances is crucial for successful adoption.
Real-World Applications Across Sectors
Healthcare, finance, and government are among the sectors actively investigating the potential of blockchain for digital identity. In healthcare, blockchain can securely store and share patient medical records, improving interoperability and data privacy. Imagine a scenario where a patient’s medical history is instantly accessible to authorized healthcare providers across different institutions, ensuring consistent and accurate care while maintaining patient control over data access.
In finance, blockchain can streamline KYC/AML processes, reducing fraud and improving efficiency. For example, banks could use blockchain to verify customer identities more quickly and securely, reducing the time and cost associated with onboarding new clients. Governments can leverage blockchain to create secure and tamper-proof digital identity systems, improving citizen services and reducing identity theft. A national digital identity system could streamline processes like voting, accessing government services, and verifying age.
Benefits and Limitations of Blockchain for Digital Identity
The advantages and disadvantages of using blockchain for digital identity vary significantly across industries. A careful evaluation is necessary before implementation.
- Benefits: Enhanced security and privacy due to cryptographic hashing and decentralization; Increased transparency and auditability of identity data; Improved interoperability and data sharing between organizations; Reduced fraud and identity theft; Greater user control over personal data.
- Limitations: Scalability challenges for large-scale deployments; Complexity of implementation and integration with existing systems; Regulatory uncertainty and lack of standardization; Potential for high initial investment costs; Need for robust infrastructure and technical expertise.
Hypothetical Scenario: Blockchain in Supply Chain Management
Let’s consider a hypothetical scenario involving a large pharmaceutical company using blockchain for tracking and verifying the authenticity of its products. This scenario illustrates how blockchain can enhance security and trust in a complex supply chain.
Imagine PharmaCorp, a global pharmaceutical company, implementing a blockchain-based system to track its drugs from manufacturing to the end consumer. Each drug package is assigned a unique digital identity on the blockchain, containing information about its manufacturing date, location, batch number, and other relevant details. This information is cryptographically secured and immutable, making it impossible to tamper with or forge.
As the drug moves through the supply chain, its journey is recorded on the blockchain, creating a transparent and auditable record. Pharmacies and hospitals can scan the package’s unique identifier to verify its authenticity and track its origin, preventing the distribution of counterfeit drugs and ensuring patient safety. This system also allows PharmaCorp to quickly identify and recall potentially contaminated batches, minimizing risk and protecting public health.
The blockchain’s decentralized nature ensures that no single entity controls the data, enhancing transparency and trust among all stakeholders.
Interoperability and Scalability

Building a truly decentralized digital identity ecosystem requires addressing significant hurdles in interoperability and scalability. Different blockchain platforms often employ unique data structures and protocols, hindering seamless communication and data exchange between systems. Similarly, the inherent limitations of blockchain technology, such as transaction speed and storage capacity, present challenges when handling the vast amounts of data associated with billions of digital identities.
Overcoming these challenges is crucial for widespread adoption and the realization of the full potential of blockchain-based digital identity.The core challenge lies in achieving seamless data exchange between disparate blockchain networks and systems. Imagine a scenario where a user’s identity is verified on one blockchain, but another service operating on a different blockchain cannot access or trust that verification.
This lack of interoperability fragments the ecosystem, limiting its utility and hindering user experience. Furthermore, the scalability of existing blockchain architectures needs significant improvement to efficiently manage the anticipated volume of transactions and data associated with a global digital identity system.
Decentralized Identifiers (DIDs) and Verifiable Credentials (VCs)
DIDs and VCs are key technologies driving interoperability. DIDs act as a unique, decentralized identifier for a user or entity, independent of any specific platform or registry. VCs, on the other hand, are digitally signed assertions that can be linked to a DID, providing verifiable proof of attributes or credentials. This combination allows users to control their data and selectively share verifiable credentials with different services, regardless of the underlying blockchain infrastructure.
For example, a user might hold a verifiable credential for their driver’s license issued on one blockchain, and then present a selectively disclosed version of this credential to a car rental service operating on a different blockchain. The system ensures the integrity and authenticity of the credential without requiring the car rental service to understand the specifics of the issuing blockchain.
Strategies for Enhancing Scalability
Several strategies can improve the scalability of blockchain solutions for digital identity. Layer-2 scaling solutions, such as state channels and sidechains, can offload transactions from the main blockchain, significantly increasing throughput. Sharding, a technique that partitions the blockchain into smaller, more manageable fragments, also enhances processing capabilities. Database solutions that integrate with blockchain for storage and retrieval of identity data can alleviate the burden on the blockchain itself, allowing it to focus on security and verification.
For example, a system might store large amounts of user profile data in a highly scalable database, while the blockchain securely stores and verifies only the cryptographic hashes of this data and the associated verifiable credentials. This architecture ensures data integrity while minimizing the load on the blockchain.
Addressing Interoperability Challenges through Standardization
Standardization efforts are crucial for achieving widespread interoperability. The development of common data formats, APIs, and protocols facilitates communication between different blockchain-based digital identity systems. Organizations like the W3C are actively working on standards for DIDs and VCs, paving the way for a more unified and interconnected ecosystem. Active participation and adherence to these standards by developers and organizations are essential for creating a truly interoperable environment where different systems can seamlessly communicate and exchange data.
Without standardization, the potential benefits of blockchain for digital identity remain largely unrealized.
Future Trends and Developments

The landscape of blockchain-based digital identity verification is constantly evolving, driven by advancements in cryptography, hardware, and regulatory frameworks. Several emerging trends promise to significantly improve the security, privacy, and usability of these systems in the coming years. These advancements will lead to more robust, scalable, and user-friendly digital identity solutions.The integration of cutting-edge cryptographic techniques and novel architectural designs will be key to unlocking the full potential of blockchain for digital identity.
This will involve addressing current limitations and paving the way for widespread adoption across various sectors.
Advancements in Zero-Knowledge Proofs and Homomorphic Encryption
Zero-knowledge proofs (ZKPs) and homomorphic encryption (HE) are poised to revolutionize digital identity management. ZKPs allow individuals to prove their identity without revealing any sensitive information beyond the bare minimum needed for verification. For example, a user could prove they are over 18 years old without disclosing their exact birthdate. Similarly, HE allows computations to be performed on encrypted data without decryption, preserving privacy throughout the process.
Imagine a scenario where a bank verifies a user’s identity and financial status without ever seeing the actual data – only the result of the computation. This significantly enhances privacy and security. The combination of ZKPs and HE will enable more sophisticated and privacy-preserving identity verification systems. For instance, a system could verify a user’s eligibility for a loan based on encrypted financial data without revealing the specifics of their income or assets to the lender.
The Future Evolution of Blockchain-Based Digital Identity Systems
Imagine a decentralized, interconnected network of identity providers, each maintaining a secure and verifiable record of individuals’ identities. This network leverages various blockchain architectures, perhaps a hybrid approach combining public and private blockchains for optimal security and scalability. Users have complete control over their data, selectively granting access to specific attributes to different entities. Verification requests are processed efficiently through advanced cryptographic techniques like ZKPs and HE, ensuring privacy is preserved throughout the process.
The system seamlessly integrates with existing authentication methods and supports a variety of identity credentials, from government-issued IDs to decentralized identifiers (DIDs). Interoperability is ensured through standardized protocols and APIs, allowing for seamless data exchange between different systems. This future system is not a monolithic entity but a robust, adaptive ecosystem that caters to diverse needs and evolves with technological advancements.
It resembles a sophisticated, secure digital vault where individuals own and manage their identities, providing greater control and security than current centralized systems. This system’s visual representation would depict a decentralized network of interconnected nodes, each representing an identity provider, with secure data flows represented by encrypted lines connecting the nodes to individual users who hold the keys to their own digital identities.
The overall architecture would be layered, with cryptographic protocols forming the foundation, blockchain technology providing the infrastructure, and user-friendly interfaces enabling easy interaction.
Ultimately, blockchain technology presents a compelling path toward a more secure and user-centric digital identity landscape. While challenges regarding scalability, interoperability, and regulation remain, the potential benefits—increased security, improved privacy, and streamlined verification processes—are undeniable. As the technology matures and adoption grows, we can expect to see even more innovative applications emerge, transforming how we interact and transact in the digital world.
The journey towards a truly decentralized and secure digital identity is underway, and blockchain is playing a pivotal role.