Understanding the concept of tokenization and its applications. – Understanding the concept of tokenization and its applications is crucial in various fields, from natural language processing (NLP) to cybersecurity. Tokenization, at its core, is the process of breaking down a larger piece of information into smaller, manageable units called “tokens.” Think of it like dissecting a sentence into individual words or a credit card number into encrypted segments.
This seemingly simple process has far-reaching implications, impacting how computers understand human language, secure sensitive data, and even revolutionize how assets are represented on a blockchain. We’ll explore the different methods, applications, and challenges associated with this powerful technique.
This guide will delve into the specifics of various tokenization methods, comparing their strengths and weaknesses across different contexts. We’ll examine its vital role in NLP tasks like sentiment analysis and machine translation, and explore how it safeguards sensitive information in security applications. Furthermore, we’ll unravel the significance of tokenization in blockchain technology, illustrating how it facilitates the creation and trading of digital assets.
Finally, we’ll discuss the future of tokenization and the ethical considerations surrounding its use.
What is Tokenization?
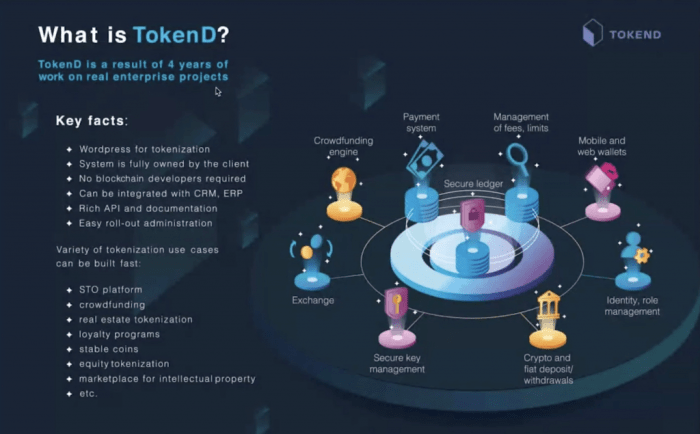
Tokenization is the process of breaking down a larger piece of text or data into smaller, meaningful units called tokens. Think of it like separating a sentence into individual words, or a paragraph into sentences. It’s a fundamental step in many data processing tasks, allowing computers to understand and work with information more effectively. This seemingly simple process is surprisingly versatile and has far-reaching applications.Tokenization Methods in Different FieldsTokenization methods vary depending on the context.
In natural language processing (NLP), the goal is often to extract words, punctuation marks, or even sub-word units like prefixes or suffixes. In cryptography, tokenization might involve replacing sensitive data with unique identifiers, or tokens, to protect privacy.
Comparison of Tokenization Techniques
Different tokenization techniques offer various trade-offs between speed, accuracy, and complexity. Choosing the right method depends heavily on the specific application and the nature of the data being processed. For instance, a simple whitespace tokenizer is fast but might struggle with punctuation or compound words, while a more sophisticated algorithm might handle these nuances better but be computationally more expensive.
Tokenization Algorithms Compared
| Algorithm Name | Description | Strengths | Weaknesses |
|---|---|---|---|
| Whitespace Tokenization | Splits text based on whitespace characters (spaces, tabs, newlines). | Simple, fast, and easy to implement. | Fails to handle punctuation correctly and struggles with compound words or hyphenated terms. |
| Regular Expression Tokenization | Uses regular expressions to define patterns for tokens. Offers greater flexibility in defining token boundaries. | Handles punctuation and complex word structures effectively. Highly customizable. | Can be complex to design and implement, potentially slower than simpler methods. Requires expertise in regular expressions. |
| NLTK Word Tokenizer (Python) | A pre-built tokenizer in the Natural Language Toolkit (NLTK) library, often used for NLP tasks. Handles various linguistic nuances. | Relatively accurate, handles many linguistic features, and integrates well with other NLTK tools. | Might be slower than simpler methods and requires familiarity with the NLTK library. |
| Stanford CoreNLP Tokenizer (Java) | A robust tokenizer from the Stanford CoreNLP suite, known for its accuracy in handling complex sentences and various languages. | High accuracy, supports multiple languages, part of a larger NLP pipeline. | More complex to set up and use, potentially resource-intensive. Requires Java environment. |
Applications of Tokenization in Natural Language Processing (NLP): Understanding The Concept Of Tokenization And Its Applications.
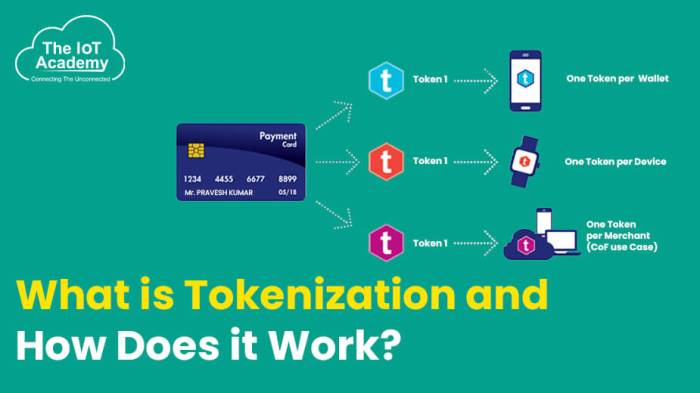
Tokenization, the process of breaking down text into individual units called tokens, is a fundamental step in many Natural Language Processing (NLP) tasks. It forms the very basis for computers to understand and process human language, enabling a wide range of applications that would otherwise be impossible. Without effective tokenization, NLP models would struggle to interpret the nuances of language, leading to inaccurate and unreliable results.
Tokenization in Text Preprocessing for NLP Tasks
Tokenization is crucial for preparing text data for various NLP tasks. It cleanses the raw text, making it suitable for analysis by algorithms. This preprocessing stage involves several steps beyond simply separating words. Consider punctuation: Should it be treated as separate tokens or discarded? Are hyphenated words single tokens or multiple?
Expand your understanding about Analyzing the energy efficiency of different blockchain networks. with the sources we offer.
How are contractions handled (“don’t” vs. “do” and “not”)? The answers to these questions heavily influence the quality of subsequent NLP analysis. For example, in sentiment analysis, correctly identifying negation words like “not” is vital for accurate sentiment prediction. Incorrect tokenization can lead to misinterpretations of the overall sentiment expressed in a sentence.
Obtain a comprehensive document about the application of Exploring the future potential of blockchain technology in supply chain management. that is effective.
Similarly, in machine translation, the correct tokenization of phrases and idioms is essential for accurate translation. A well-defined tokenization strategy ensures consistency and reliability across the entire NLP pipeline.
Tokenization’s Contribution to Improving the Accuracy of Sentiment Analysis
Accurate sentiment analysis relies heavily on correctly identifying and interpreting individual words and phrases. Tokenization directly impacts this accuracy. For instance, consider the sentence: “This product is not bad.” Incorrect tokenization might treat “not bad” as a single token, potentially leading to a positive sentiment classification. However, proper tokenization separates “not” and “bad,” allowing the algorithm to correctly identify the negative sentiment.
Furthermore, tokenization helps in handling negations and intensifiers. Words like “very,” “extremely,” or “slightly” modify the sentiment expressed by other words. Proper tokenization allows the NLP model to capture these nuances, improving the accuracy of the overall sentiment prediction. Advanced tokenization techniques, such as subword tokenization (e.g., using Byte Pair Encoding or WordPiece), can further enhance accuracy by handling rare words and out-of-vocabulary terms more effectively.
Tokenization’s Impact on Machine Translation and its Challenges
Tokenization plays a pivotal role in machine translation. The process of translating text from one language to another involves breaking down the source text into tokens, translating each token individually or in groups, and then recombining them to form the target language text. However, challenges arise due to differences in language structures. Languages like Chinese or Japanese don’t use spaces to separate words, requiring more sophisticated tokenization techniques.
Furthermore, morphological differences between languages (e.g., verb conjugations, noun declensions) can impact tokenization and subsequent translation accuracy. Ambiguity in word boundaries or the presence of idioms and collocations further complicates the process. Advanced tokenization methods, combined with contextual understanding, are crucial for overcoming these challenges and achieving high-quality machine translation.
Workflow Diagram for Tokenizing Text for Sentiment Analysis, Understanding the concept of tokenization and its applications.
The following diagram illustrates a typical workflow:“`[Start] –> [Text Input (e.g., “This movie is absolutely terrible!”)] –> [Lowercasing (e.g., “this movie is absolutely terrible!”)] –> [Punctuation Removal (e.g., “this movie is absolutely terrible”)] –> [Tokenization (e.g., [“this”, “movie”, “is”, “absolutely”, “terrible”])] –> [Stop Word Removal (e.g., [“movie”, “absolutely”, “terrible”])] –> [Sentiment Analysis (e.g., Negative Sentiment)] –> [Output (e.g., Negative)] –> [End]“`Each step is clearly defined, transforming the raw text into a processed form suitable for sentiment analysis.
Lowercasing ensures case-insensitive analysis. Punctuation removal simplifies the tokens. Tokenization separates the text into individual words. Stop word removal eliminates common words (like “is,” “a,” “the”) that usually don’t carry significant sentiment. Finally, the sentiment analysis algorithm processes the remaining tokens to determine the overall sentiment.
Tokenization in Security and Cryptography
Tokenization is a powerful data security technique that replaces sensitive data with non-sensitive equivalents, called tokens. These tokens hold no intrinsic value on their own and are essentially meaningless without a corresponding decryption key. This process offers a robust way to protect sensitive information while still allowing for its use in various applications. Think of it like using a code word – the code word itself doesn’t reveal the original information, but with the right key, you can easily retrieve it.Tokenization offers a strong layer of security by decoupling sensitive data from its usage.
This means even if a database is breached, the exposed tokens are worthless without the decryption key. This significantly reduces the risk of data breaches leading to identity theft, financial fraud, and regulatory penalties. It’s a proactive approach, safeguarding data at rest and in transit.
Protection of Personally Identifiable Information (PII)
Tokenization effectively protects Personally Identifiable Information (PII) by replacing sensitive data elements like names, addresses, social security numbers, and credit card details with unique, non-sensitive tokens. These tokens are stored separately from the original data, often in a secure token vault. This ensures that even if the token database is compromised, the actual PII remains safe. The system only needs access to the tokens to process transactions or queries, leaving the original PII untouched and protected.
For instance, instead of storing “John Doe” and his credit card number, the system stores a token like “TK12345” linked to John Doe’s data in a secure vault. Accessing John’s information requires retrieving the original data using TK12345 and the decryption key.
Comparison with Other Data Masking Techniques
Tokenization differs from other data masking techniques, such as data anonymization and pseudonymization, in its reversibility. Anonymization permanently removes identifying information, making it irreversible. Pseudonymization replaces identifying information with pseudonyms, but these pseudonyms might be linked back to the original data with enough effort. Tokenization, however, offers a reversible process. The original data can be retrieved from the token using the decryption key, making it suitable for applications where access to the original data is still required.
This reversibility is a key advantage for regulatory compliance and data recovery purposes. For example, if a financial institution needs to access a customer’s full credit card information for a fraud investigation, tokenization allows this access while keeping the data secure at all other times.
Common Use Cases for Tokenization in Securing Payment Card Information
Tokenization is widely used to protect payment card information. The following points highlight some common applications:
- Protecting card details stored in databases and applications.
- Securing card data during online transactions.
- Enabling secure storage and processing of card information for recurring billing.
- Facilitating secure data sharing between merchants and payment processors.
- Complying with payment card industry data security standards (PCI DSS).
- Protecting card data during data backups and archiving.
Tokenization in Blockchain Technology

Tokenization in blockchain technology revolutionizes how we represent and interact with assets. It bridges the gap between the physical and digital worlds by transforming real-world assets into digital tokens, each representing a fractional or whole ownership stake. This allows for easier trading, fractional ownership, and increased liquidity for a wide range of assets.Tokenization leverages the immutable and transparent nature of blockchain to create a secure and verifiable record of asset ownership.
This eliminates intermediaries, reduces transaction costs, and increases efficiency in various asset classes.
Representing Assets on a Blockchain
Tokenization represents assets on a blockchain through the creation of unique digital tokens. These tokens are cryptographic representations of the underlying asset, storing crucial information such as ownership details, asset characteristics, and any associated rights. The blockchain acts as a distributed ledger, ensuring that all transactions involving these tokens are recorded securely and transparently, verifiable by all participants.
This provides a high degree of trust and eliminates the need for central authorities to manage ownership records. For example, a painting could be tokenized, with each token representing a percentage of ownership. The blockchain would track the ownership of each token, ensuring that the transfer of ownership is secure and transparent.
Examples of Digital Asset Creation and Trading
Several examples illustrate how tokenization facilitates the creation and trading of digital assets. Security tokens, representing equity in a company, allow for fractional ownership and easier trading of company shares. Utility tokens provide access to a product or service, such as discounts or exclusive content. Non-fungible tokens (NFTs) represent unique digital or physical assets, like artwork or collectibles, ensuring authenticity and ownership.
These tokens are traded on decentralized exchanges (DEXs) or other platforms built on blockchain technology, offering a more efficient and transparent trading environment than traditional methods. For instance, a real estate property could be tokenized, allowing investors to buy and sell fractional ownership through tokens on a blockchain-based platform.
Tokenizing Real-World Assets: A Detailed Process
Tokenizing a real-world asset involves several key steps. First, the asset needs to be thoroughly vetted and assessed to determine its value and characteristics. Legal compliance is crucial, ensuring the process adheres to all relevant regulations. Next, the asset is represented digitally, often through smart contracts on the blockchain. These smart contracts define the rules governing the tokens, such as ownership transfer, voting rights, and any other relevant conditions.
Then, the asset is divided into tokens, each representing a specific portion of ownership. These tokens are then issued and distributed to investors or other stakeholders. Finally, the tokens are traded on a suitable platform, often a decentralized exchange, facilitating liquidity and transparency in the market. The entire process is recorded on the blockchain, creating an auditable trail of ownership and transactions.
Tokenizing a Physical Asset: A Conceptual Illustration
Let’s imagine tokenizing a classic car. Step 1: Asset Appraisal and Legal Compliance: The car is professionally appraised to determine its value. Legal counsel ensures all necessary documentation and compliance are met before proceeding. Step 2: Digital Representation: The car’s details—make, model, VIN, photographs, and any relevant documentation—are securely stored and linked to a unique identifier. Step 3: Smart Contract Creation: A smart contract is created on a blockchain.
This contract defines the terms of ownership, including rules for transferring tokens, voting rights (if applicable), and any other relevant conditions. Step 4: Tokenization: The ownership of the car is divided into, say, 100 tokens. Each token represents 1% ownership of the car. Step 5: Token Distribution: The tokens are distributed to investors, who now hold fractional ownership of the classic car. Step 6: Blockchain Recording: Every transaction involving these tokens—buying, selling, or transferring—is recorded on the blockchain, creating a transparent and immutable record of ownership.The blockchain acts as a secure and transparent ledger, tracking the ownership of each token and ensuring the legitimacy of all transactions.
This allows for easy trading and fractional ownership of the classic car, increasing liquidity and accessibility for a wider range of investors.
Challenges and Future Trends in Tokenization

Tokenization, while powerful, isn’t without its hurdles. Different methods present unique challenges, and ethical considerations are paramount as its applications expand. Looking ahead, advancements in technology, especially AI, promise to significantly refine and broaden the capabilities of tokenization.
The effectiveness of tokenization hinges heavily on the chosen method. Word-based tokenization, for instance, struggles with handling contractions and compound words, leading to information loss or ambiguity. Subword tokenization, while addressing some of these issues, can create inconsistencies in representation, particularly with rare words or domain-specific terminology. Character-level tokenization, although robust, often results in excessively long sequences, increasing computational costs and potentially obscuring meaningful linguistic units.
Furthermore, the optimal tokenization strategy often varies depending on the specific NLP task and the characteristics of the language being processed.
Limitations and Challenges of Different Tokenization Methods
Different tokenization approaches present unique limitations. For example, simple whitespace tokenization fails to handle punctuation correctly and struggles with languages that don’t rely on spaces to separate words. More sophisticated methods, such as rule-based tokenization, require extensive linguistic expertise and manual rule creation, which can be time-consuming and prone to errors. Statistical methods, while more adaptable, may require large amounts of training data and can be computationally expensive.
Finally, the choice of tokenization method can significantly impact the performance of downstream NLP tasks, underscoring the importance of careful selection and evaluation.
Ethical Considerations in Tokenization
The increasing use of tokenization raises significant ethical concerns. Bias embedded in training data can be amplified during tokenization, leading to discriminatory outcomes in applications like sentiment analysis or machine translation. For example, if a dataset overrepresents certain demographics, the resulting tokenization scheme might perpetuate those biases in downstream tasks. Privacy is another key concern, particularly in applications involving sensitive personal information.
Tokenization, while potentially anonymizing data, may not always fully protect against re-identification, especially if metadata or contextual information is available. Robust anonymization techniques are crucial to mitigate these risks. Transparency and accountability in the development and deployment of tokenization systems are vital for building trust and ensuring responsible use.
Future Developments and Advancements in Tokenization Technology
The future of tokenization looks bright, with several promising areas of development. We can anticipate more sophisticated algorithms that adapt dynamically to different languages and domains, automatically learning optimal tokenization strategies based on the specific task and data. Advancements in unsupervised and semi-supervised learning will reduce the reliance on large, labeled datasets, making tokenization more accessible and applicable to low-resource languages.
Furthermore, research into contextualized tokenization, which considers the surrounding words and context when generating tokens, promises to improve the accuracy and robustness of NLP systems. This might involve leveraging transformer-based models or other deep learning architectures to capture richer semantic information during the tokenization process.
Advancements in AI and their Impact on Tokenization Techniques
Artificial intelligence, particularly deep learning, is poised to revolutionize tokenization. AI-powered systems can learn complex patterns in language data and automatically generate optimal tokenization schemes tailored to specific tasks and datasets. For instance, neural language models can be trained to predict optimal tokenization boundaries based on the context of surrounding words, improving accuracy and reducing ambiguity. Reinforcement learning techniques could further optimize tokenization strategies by rewarding models for generating tokens that improve the performance of downstream NLP tasks.
The development of more efficient and scalable algorithms will also be crucial, allowing for faster processing of large datasets and real-time tokenization in applications requiring low latency.
From enhancing the accuracy of AI-powered language processing to securing sensitive financial data and revolutionizing asset representation on blockchains, tokenization proves to be a versatile and transformative technology. While challenges remain, particularly regarding ethical considerations and the potential for misuse, the ongoing advancements in this field promise even more innovative applications in the future. Understanding the core concepts and diverse applications of tokenization is essential for anyone navigating the increasingly digital world.