How to protect your privacy when using cryptocurrencies. – How to protect your privacy when using cryptocurrencies? It’s a crucial question in the increasingly digital world. Cryptocurrency, while offering exciting possibilities, also presents unique privacy challenges. This guide will walk you through essential strategies to safeguard your personal information and maintain your anonymity while navigating the crypto landscape. We’ll cover everything from choosing the right wallet to understanding transaction privacy techniques and staying ahead of emerging security threats.
Protecting your privacy in the crypto world involves a multi-pronged approach. It’s not just about securing your wallet; it’s about understanding the security features of exchanges, employing robust online privacy practices, and staying informed about the latest scams and vulnerabilities. This guide aims to empower you with the knowledge and tools to navigate the crypto space confidently and securely.
Understanding Transaction Privacy
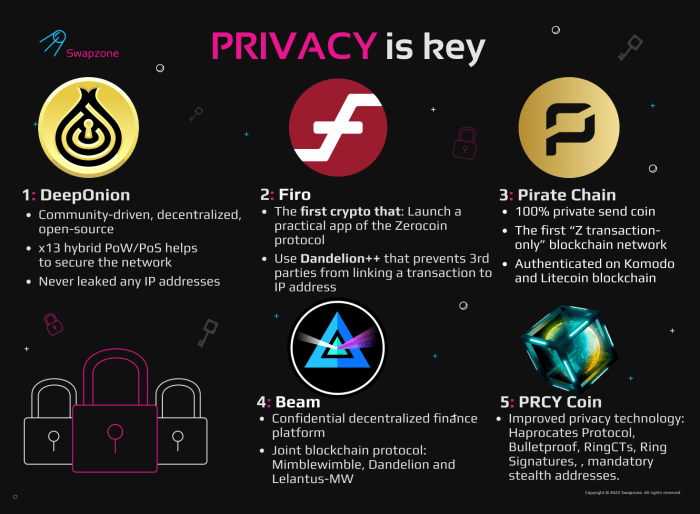
Protecting your privacy when using cryptocurrencies goes beyond just securing your wallet. Understanding how transactions are processed and the various levels of privacy offered by different coins is crucial for maintaining your anonymity. This section delves into the techniques available and the trade-offs involved.Transaction privacy in the cryptocurrency world is a spectrum, not a binary. Some cryptocurrencies are designed with strong privacy features built-in, while others offer minimal anonymity.
The level of privacy you achieve depends on the cryptocurrency you choose, the tools you use, and how carefully you manage your transactions.
Transaction Privacy Techniques
Several methods aim to enhance transaction privacy. Mixing services, for instance, pool together multiple transactions, obscuring the origin and destination of individual funds. Privacy coins, on the other hand, employ advanced cryptographic techniques to inherently mask transaction details from the public blockchain. These techniques offer varying degrees of protection, and the effectiveness often depends on the specific implementation and widespread adoption.
Comparison of Cryptocurrency Privacy Levels
The privacy levels offered by different cryptocurrencies vary significantly. Bitcoin, for example, while pseudonymous, leaves a traceable trail of transactions on the public blockchain. Monero, conversely, prioritizes privacy through its ring signatures and stealth addresses. Below is a comparison illustrating the spectrum of privacy:
| Cryptocurrency | Privacy Level | Transaction Traceability | Privacy Features |
|---|---|---|---|
| Bitcoin | Low | High | Pseudonymous addresses |
| Ethereum | Low | High | Public transaction history |
| Monero | High | Low | Ring signatures, stealth addresses |
| Zcash | Medium to High | Medium to Low | Shielded transactions (optional) |
Privacy vs. Regulatory Compliance
There’s an inherent tension between enhancing transaction privacy and adhering to regulatory compliance. Strong privacy features, while protecting individual users, can also make it more difficult for law enforcement agencies to track illicit activities. Regulations vary widely across jurisdictions, and choosing a cryptocurrency with high privacy features may lead to difficulties in certain regions or exchanges. The decision to prioritize privacy often involves weighing the potential risks of non-compliance against the need for anonymity.
For example, some jurisdictions actively monitor cryptocurrency transactions, making high-privacy coins potentially problematic for users in those areas. Conversely, using transparent cryptocurrencies might expose sensitive financial information to unwanted scrutiny. Understanding these trade-offs is critical for making informed decisions.
Staying Informed About Security Threats: How To Protect Your Privacy When Using Cryptocurrencies.

Staying informed about cryptocurrency security threats is crucial for protecting your assets. The crypto landscape is constantly evolving, with new vulnerabilities and scams emerging regularly. Proactive learning is your best defense against financial loss. By staying updated, you can make informed decisions and avoid common pitfalls.Staying updated on cryptocurrency security threats requires diligent effort and awareness of credible information sources.
It’s essential to distinguish between legitimate security alerts and misinformation.
Reputable Sources for Cryptocurrency Security Information
To stay ahead of the curve, rely on trusted sources for accurate and timely information. These sources provide in-depth analysis and reports on emerging threats. Ignoring this step leaves you vulnerable to exploitation.
- Major Cryptocurrency Exchanges (e.g., Coinbase, Binance): These exchanges often publish security advisories and warnings about scams targeting their users.
- Security Research Firms (e.g., SlowMist, PeckShield): These firms specialize in identifying and analyzing vulnerabilities in blockchain technology and cryptocurrency platforms.
- Blockchain Security Auditors (e.g., CertiK, Quantstamp): These firms conduct audits of smart contracts and other blockchain-related projects, identifying potential security risks.
- Reputable Cryptocurrency News Outlets (e.g., CoinDesk, Cointelegraph): These outlets report on significant security incidents and emerging threats within the cryptocurrency industry.
- Official Cryptocurrency Project Websites and Blogs: Many cryptocurrency projects maintain blogs or websites where they publish security updates and warnings.
Common Cryptocurrency Scams and Avoidance Strategies, How to protect your privacy when using cryptocurrencies.
Cryptocurrency scams are pervasive and constantly evolving. Understanding common tactics is vital for protection. Ignoring these risks can lead to significant financial losses.
- Phishing Scams: These involve deceptive emails, messages, or websites designed to steal your login credentials or private keys. Always verify the authenticity of any communication before clicking links or providing sensitive information.
- Fake Cryptocurrency Exchanges and Wallets: Scammers create fake exchanges or wallets that look legitimate but steal your funds. Only use well-established and reputable platforms.
- Investment Scams (e.g., Pump and Dump Schemes): These involve artificially inflating the price of a cryptocurrency and then selling it off at a profit, leaving investors with losses. Conduct thorough research before investing in any cryptocurrency.
- Romance Scams: Scammers build relationships with victims online to gain their trust before asking for cryptocurrency investments or donations.
- Giveaway Scams: These involve promises of free cryptocurrency in exchange for sending a small amount of cryptocurrency or providing personal information. Legitimate cryptocurrency projects rarely offer giveaways.
Lifecycle of a Typical Cryptocurrency Scam
This visual representation illustrates the typical stages of a cryptocurrency scam:
Stage 1: Initial Contact. The scammer initiates contact through various channels (e.g., social media, email, fake websites). They might pose as a legitimate entity or build rapport with the victim.
Stage 2: Building Trust. The scammer spends time cultivating trust with the victim, often through flattery, fabricated stories, or promises of high returns. This stage can last for weeks or months.
Stage 3: The Request. The scammer makes a request for cryptocurrency, often disguised as an investment opportunity, donation, or a supposed requirement for accessing a reward.
Stage 4: The Transfer. The victim transfers cryptocurrency to the scammer’s wallet.
Stage 5: Disappearance. The scammer disappears after receiving the cryptocurrency, leaving the victim with no recourse.
Stage 6: (Optional) Further Exploitation. In some cases, scammers might continue to contact the victim with further requests or exploit their personal information for other fraudulent activities.
Ultimately, protecting your privacy when using cryptocurrencies requires vigilance and a proactive approach. By carefully selecting your wallet, diligently managing your private keys, employing strong online security practices, and staying informed about evolving threats, you can significantly reduce your risk and maintain a greater degree of anonymity. Remember, your digital security is an ongoing process, not a one-time fix. Regularly review your security measures and stay updated on the latest best practices to ensure your continued protection in the ever-changing world of cryptocurrency.
Obtain direct knowledge about the efficiency of The role of smart contracts in the development of decentralized applications (dApps) on various blockchains. through case studies.
Browse the implementation of The potential use of blockchain technology in voting systems. in real-world situations to understand its applications.