How to use blockchain technology to improve data security. This guide dives into the exciting world of blockchain and its potential to revolutionize data protection. We’ll explore how this decentralized technology, with its cryptographic underpinnings and immutable ledger, offers a powerful defense against data breaches and unauthorized access. Get ready to learn how blockchain’s unique features can safeguard your valuable information.
We’ll cover the core concepts of blockchain, including cryptography, immutability, and consensus mechanisms, explaining how they work together to enhance security. We’ll also look at real-world applications across various industries, showcasing successful implementations and addressing potential challenges. By the end, you’ll have a solid understanding of how to leverage blockchain technology for stronger data security.
Introduction to Blockchain and Data Security
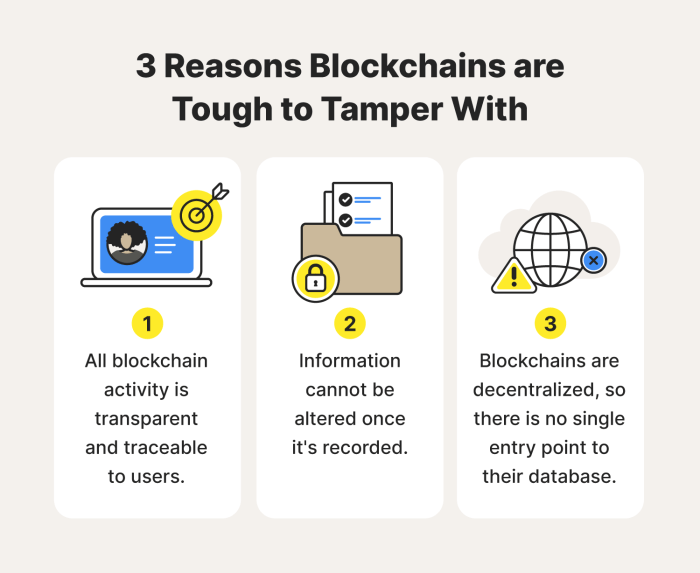
Blockchain technology offers a revolutionary approach to data security, fundamentally altering how we store and manage sensitive information. Unlike traditional databases, which are centralized and vulnerable to single points of failure, blockchain utilizes a decentralized, distributed ledger system to enhance data integrity and security. This means data isn’t stored in one place but is replicated across a network of computers, making it significantly more resilient to attacks and breaches.Blockchain’s core strength lies in its cryptographic security and its immutable nature.
Find out further about the benefits of The potential use of blockchain technology in healthcare data management. that can provide significant benefits.
Each transaction or data entry is linked to the previous one using cryptographic hashing, creating a chain of blocks. Altering any single block requires altering all subsequent blocks, a computationally infeasible task. This makes tampering with data extremely difficult, providing a high level of data integrity. This contrasts sharply with centralized systems where a single point of compromise can compromise the entire database.
Blockchain’s Decentralized Nature and Enhanced Data Security
The decentralized nature of blockchain is key to its superior security. In a centralized system, all data resides on a single server, making it a prime target for hackers. A successful attack can result in the loss or corruption of all data. However, in a blockchain network, data is distributed across numerous nodes. Even if some nodes are compromised, the majority of the network remains intact, ensuring data availability and preventing complete data loss.
Finish your research with information from The potential for blockchain technology to revolutionize the voting process..
This redundancy significantly increases resilience against cyberattacks, natural disasters, and other threats. The distributed consensus mechanisms, like Proof-of-Work or Proof-of-Stake, further enhance security by requiring agreement from a majority of nodes before any changes are accepted onto the blockchain.
Examples of Data Breaches and Blockchain Mitigation
Consider the 2017 Equifax data breach, where the personal information of nearly 150 million people was exposed due to a vulnerability in their systems. A blockchain-based system could have mitigated this by storing sensitive data in a decentralized, encrypted manner. Even if one node were compromised, the majority of the data would remain secure and inaccessible to the attackers.
Similarly, the 2013 Target data breach, which involved the theft of millions of credit card numbers, could have been prevented or significantly reduced in severity by utilizing blockchain technology for transaction processing and customer data storage. The decentralized and immutable nature of blockchain would have made it significantly harder for attackers to access and manipulate sensitive data. The use of cryptographic techniques further enhances security, protecting data from unauthorized access even if a node is compromised.
Future Trends and Developments in Blockchain Data Security
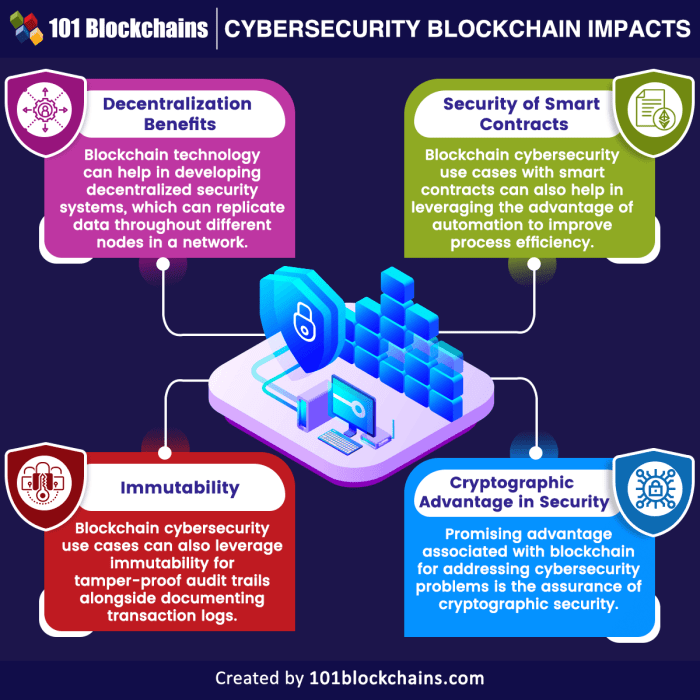
Blockchain technology is constantly evolving, and its application in data security is rapidly expanding. New trends are emerging that promise even greater levels of protection and efficiency, moving beyond the initial concepts and into sophisticated, integrated systems. This section explores these advancements and their potential impact.The integration of blockchain with other technologies is driving significant improvements in data security.
These synergistic relationships are creating powerful new security paradigms.
Blockchain and Artificial Intelligence Synergy
AI and machine learning algorithms are being incorporated into blockchain systems to enhance security in several ways. For instance, AI can analyze vast amounts of transaction data to identify and flag suspicious activity in real-time, far exceeding the capabilities of traditional fraud detection methods. This proactive approach can prevent breaches before they occur. Furthermore, AI can help optimize blockchain consensus mechanisms, making them more efficient and resilient against attacks.
Consider, for example, the use of AI in detecting anomalies in transaction patterns, which could indicate a malicious actor attempting to manipulate the system. This real-time analysis allows for immediate intervention, preventing significant damage.
Blockchain and Internet of Things Integration
The Internet of Things (IoT) generates massive amounts of data, much of which is sensitive. Integrating blockchain with IoT devices creates a secure and transparent system for managing and sharing this data. Blockchain can provide a tamper-proof record of data provenance, ensuring the authenticity and integrity of information collected from IoT sensors. Imagine a smart city using blockchain to track and verify the authenticity of environmental data collected by various sensors.
This ensures that the data used for city planning and resource management is accurate and reliable, preventing potential misuse or manipulation.
Advancements in Cryptography
The underlying cryptography of blockchain is constantly being refined. Post-quantum cryptography, designed to withstand attacks from quantum computers, is a significant development. This is crucial as quantum computing advances, posing a potential threat to current cryptographic algorithms. Implementing post-quantum cryptography will ensure the long-term security of blockchain-based data storage. Another advancement is the development of more efficient and secure zero-knowledge proof protocols.
These protocols allow for verification of information without revealing the underlying data, enhancing privacy and security. For example, a user could prove their identity without disclosing their personal details, maintaining confidentiality while still ensuring secure access.
Potential Benefits and Risks of Future Blockchain Data Security
The integration of blockchain with other technologies presents both significant opportunities and potential challenges. It’s vital to understand both sides of the coin.
Before listing the points, it’s important to note that while blockchain offers significant advantages, its implementation requires careful planning and consideration of potential vulnerabilities. The technology is not a silver bullet solution and needs to be integrated strategically.
- Benefit: Enhanced data integrity and immutability, leading to greater trust and transparency.
- Benefit: Improved data security through cryptographic techniques and decentralized architecture, reducing single points of failure.
- Benefit: Increased efficiency and automation in data management and access control.
- Benefit: Enhanced privacy through techniques like zero-knowledge proofs.
- Risk: The complexity of blockchain technology can make implementation and maintenance challenging.
- Risk: Scalability issues can limit the adoption of blockchain for large-scale data storage and processing.
- Risk: 51% attacks, though unlikely in well-established blockchains, remain a theoretical vulnerability.
- Risk: Smart contract vulnerabilities can be exploited by malicious actors, potentially compromising data security.
Illustrative Example: Secure Data Management System using Blockchain: How To Use Blockchain Technology To Improve Data Security.
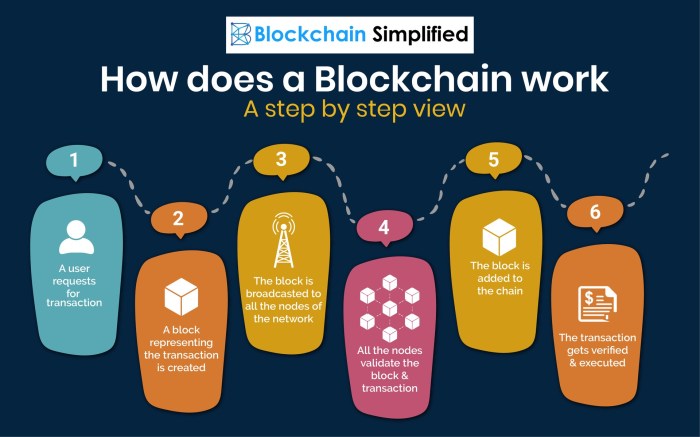
This section details a conceptual architecture for a secure data management system leveraging blockchain technology. We’ll explore its components, data flow, and user interaction, highlighting the roles of cryptographic hashing and digital signatures. This system aims to enhance data integrity, transparency, and auditability.
System Architecture, How to use blockchain technology to improve data security.
The system comprises several key components: a blockchain network, a data storage layer, a user interface, and smart contracts. The blockchain network provides a decentralized and immutable ledger for recording data transactions. The data storage layer can be a distributed file system or cloud storage, storing the actual data referenced by the blockchain. The user interface allows users to interact with the system, while smart contracts automate data management processes and enforce access control.
These components interact through APIs, ensuring secure and efficient data flow. Data entry triggers a transaction, creating a new block on the blockchain that contains a cryptographic hash of the data and a digital signature for verification. Data retrieval involves querying the blockchain for the hash, locating the corresponding data in the storage layer, and verifying the digital signature.
Data Entry, Storage, Retrieval, and Verification
Data entry begins with a user submitting data through the user interface. This data is then cryptographically hashed using a secure hashing algorithm like SHA-256. The hash, along with metadata like timestamp and user ID, is packaged into a transaction and added to the blockchain network. The actual data is stored separately in the data storage layer. Retrieval involves querying the blockchain for a specific data entry using its hash or other identifying information.
Once located, the blockchain provides the hash, which is then used to retrieve the data from the storage layer. The digital signature associated with the data entry is then verified to ensure data integrity and authenticity. This process ensures only authorized users can access and modify data. Any attempt to tamper with the data will result in a mismatch between the hash in the blockchain and the hash of the altered data.
User Interaction
Let’s imagine a scenario where a hospital wants to securely manage patient medical records. A doctor uses the user interface to input a new patient record. This initiates the following steps:
1. Data Input
The doctor enters the patient’s data (name, age, medical history, etc.) into the system.
2. Hashing
The system automatically generates a cryptographic hash of the entered data.
3. Digital Signature
The doctor digitally signs the transaction using their private key, ensuring authenticity and non-repudiation.
4. Blockchain Transaction
The transaction, containing the hash, digital signature, and metadata, is added to the blockchain.
5. Data Storage
The actual patient record is stored securely in the data storage layer.
6. Data Retrieval
Another doctor needs to access the patient’s record. They query the system using the patient’s ID or other identifier.
7. Hash Verification
The system retrieves the hash from the blockchain and compares it to the hash of the retrieved data. If they match, data integrity is confirmed.
8. Signature Verification
The system verifies the digital signature to ensure authenticity.
9. Data Access
If both verification steps succeed, the doctor gains access to the patient’s record.This process ensures data integrity, transparency, and auditability, providing a secure and reliable system for managing sensitive medical information. The immutability of the blockchain prevents unauthorized alteration of records, and the cryptographic hashing and digital signatures provide strong security against tampering.
Ultimately, mastering how to use blockchain technology to improve data security involves understanding its core principles and applying them strategically. While challenges exist, the potential benefits – enhanced data integrity, improved trust, and reduced vulnerability to attacks – are significant. As blockchain technology continues to evolve, its role in safeguarding sensitive data will only become more crucial. By embracing this innovative approach, organizations and individuals can build a more secure and resilient digital future.